The Polish startup Secfense has a chance to play an important role in adopting strong authentication in large and medium-sized companies and become a global user access security broker. Companies of any size can implement two-factor authentication (2FA) using time-based one-time passwords (TOTP) or universal 2nd Factor authentication (U2F) using security keys.
– Without hiring programmers.
– Without access to third-party application code.
– Without any hidden costs.
Fast, easy and convenient.
Why 2FA hasn’t become a standard yet?
The implementation of the second login component in small projects without the participation of programmers (even using free GitHub libraries) is time-consuming, expensive and complicated. Large social platforms, including the fintech industry, have long been trying to popularize a two-factor authentication method that is safer than SMS. The text-based method has already been compromised in the past, so it’s better to use strong authentication based on cryptographic keys and the FIDO standard.
Still, two-factor authentication has not become a natural choice where it should be. 2FA is still missing in many organizations, e.g. in large partner networks for online publishers, or even in online accounting services. Some companies providing accounting services are offering 2FA with a more expensive subscription plan.
The most popular forms of two-factor authentication (alternative to SMS-based OTP) use a program-generated one-time password, also called TOTP (Time-based One-time Password) and the example of it is Google Authenticator or Microsoft Authenticator to name a few.
Before the business realized that some of the 2FA methods are not 100% resistant to attacks, organizations have already started working on an improved, open standard, i.e. FIDO U2F (based on public-key cryptography) and the later FIDO2 (which also integrates local authentication devices). Work on the FIDO U2F authentication standard was started by Google and Yubico – a manufacturer of hardware security keys, and then developed by a consortium of hundreds of technology companies called FIDO Alliance (https://fidoalliance.org), which is why you can often find the FIDO record U2F or FIDO2.
With a FIDO-compliant security key (that, for example, supports NFC wireless communication technology at close range), you can log into online services just like you would on a computer:

This secure login solution has been successfully implemented on a very large scale, e.g. by the UK government, the Turkish government, many international banks, and even the US Department of Defense.
The U2F protocol is supported by, among others Amazon in its AWS service, Microsoft in business products, BitBay cryptocurrency exchange, numerous CMS systems, SaaS security service providers, social platforms, password managers and much more. A full list of manufacturers who integrated their solutions with FIDO is available here .
The authentication method using a hardware token guarantees one of the safest ways to log into websites, servers, Windows home systems, and production servers. Recently, OpenSSH version 8.2 also offers official support for FIDO.
Secfense is consolidating available multi-factor authentication methods
Employees in organizations, privately or on business instructions, rarely use secure methods to log into company IT resources. The problem is that it’s difficult to control all people. Then there is fragmentation, scattering of passwords and logins per employee. Even more difficult is to force people to comply with the policy of using at least a one-time password generated by the smartphone in the FreeOTP, Microsoft Authenticator, Duo Security or other application.
Using 2FA is much safer than relying on your login and password. In addition, the situation is catastrophic if the Internet resource exposed to the Internet is not secured by at least a second component based on TOTP – and preferably if logging into the resource was in accordance with the FIDO standard.
The implementation of such security can be expensive and complicated, and often impossible, if the application has a closed code or the program is managed by an external company. And this is where Secfense comes in handy.
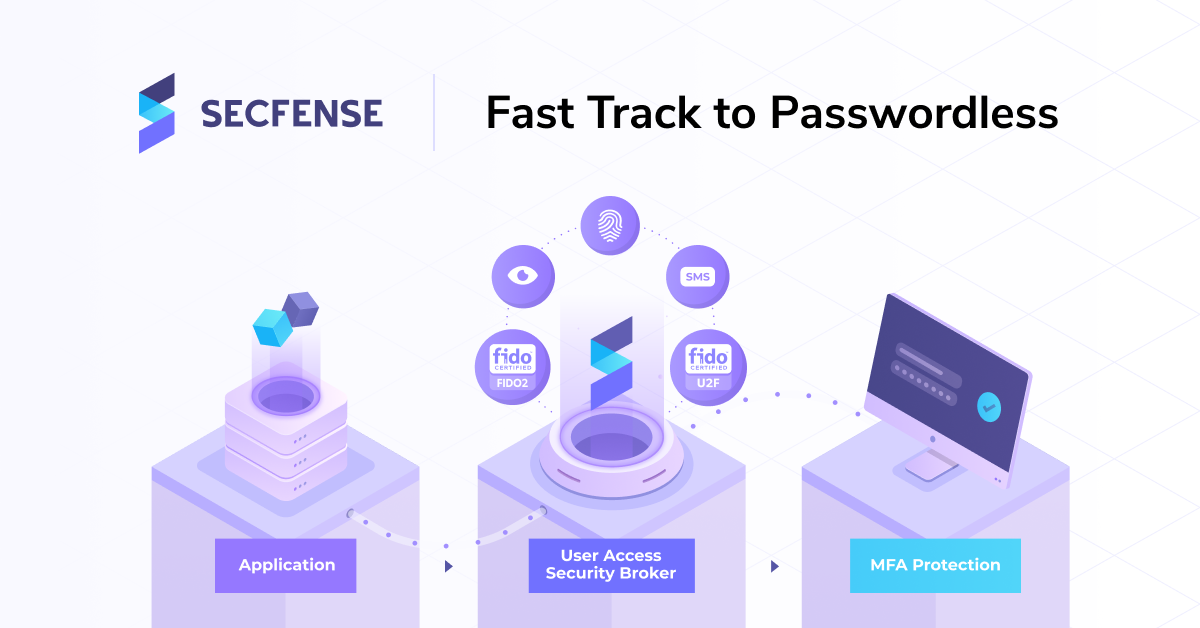
The implementation of the Secfense User Access Security Broker (UASB) in the organization’s infrastructure means that a web application or online service that is available through a browser does not need to have two-factor login implemented. This is what Secfense is, i.e. the broker, the link between available user authorization technologies without affecting the operation of external applications.
Secfense broker supports all available multi-factor authentication methods. So regardless of whether the company decides to use OTP / TOTP, cryptographic keys working in the FIDO standard (Yubikey, Google Titan Security Key, Nitrokey, other), or the FIDO2 authentication method based on local authenticators, each of the methods available on the market can be provided by Secfense for any application inside the organization.
Secfense User Access Security Broker is an intermediary in the application and enforcement of strong two-factor authentication on employees. The product can secure access to applications where 2FA implementation by traditional means is too expensive or impossible. Secfense is perfectly suited to protect e.g. PLC control systems and SCADA industrial systems in Polish factories that are not prepared for modern cyberwar.
The implementation of Secfense brings many benefits to every organization:
- secures access to the resource or control panel from unauthorized persons (protects against phishing, MITM and session theft attacks)
- monitors, records and records user session (increases transparency and facilitates detection of an attack from within)
- gives the administrator freedom to choose the method of strong authentication as well as to specify the login policy
An example of Secfense implementation is the product implementation in a large rail transport company. The goal that the client wanted to achieve was to build a virtual layer of protection for application users and IT infrastructure devices, in which it is possible to implement any component of strong authentication. The result was:
- reducing the cost of integrating 2FA with applications
- the possibility of implementing 2FA in places where it was not possible to tamper with the application code, device firmware or caused high costs
- the ability to quickly implement 2FA and quickly change 2FA in the context of any web-application without the involvement of programmers
- central management of user security methods and 2FA components in the context of web applications.
The applications and client infrastructure of the above example is located in two parallel data center centers. When implementing Secfense UASB, great emphasis was placed on high system availability and access to protected applications.
Why use Secfense?
Secfense User Access Security Broker should be used to add a layer of strong authentication. EVERYWHERE. Even where it wasn’t possible before.
The increase in the number of online services requires people to set up more and more online accounts. Somehow you need to control and keep secure all your passwords and logins. This means that the employee must remember way too many credentials, which paves the way for a dangerous habit – using the same passwords everywhere. Hackers love this trend because if the username and password are intercepted from one leak, it is highly likely that the same credentials were used to set up other accounts.
Password manager is an obligatory minimum, but theory and practice often pass each other along the way. Yubico has published a report on password management in organizations. The main conclusions from the report are not optimistic (the survey was attended by 2507 security specialists from Australia, France, Germany, Sweden, Great Britain and the United States, as well as 563 individual users).
There is still a lot to be done about risk awareness – both IT professionals as well as casual online users have bad password management practices. According to the study, many specialists do not even use two-factor authentication (2FA):
- 50% of professionals and 39% of individual users log into private websites at the workplace using their private passwords.
- 59% of specialists say that the password management policy in their organization is based on human memory (no password managers!).
- Less than half (46%) of IT professionals say that their businesses require the use of 2FA to access company accounts.
- 62% of respondents do not take the necessary steps to protect information on mobile devices.
- 37% of organizations that implement 2FA to secure company accounts rely on mobile authentication applications, and 28% rely on SMS codes.
- 23% of people think that authentication methods using SMS or 2FA mobile applications are very inconvenient.
- 56% of people using a mobile device to access work-related resources do not use 2FA.
It turns out that IT employees who are considered “specialists” do not use the safe authentication methods guaranteed by hardware tokens. This confirms the low awareness of password management practices, lack of knowledge about attacks intercepting 2FA login and insufficient knowledge of the advantages of keys, which significantly simplify login process and makes it much more secure.
The reasonable response to that can be the Secfense product, which adds the strong 2FA to the authentication process, including currently the safest cryptographic keys and built-in FIDO2-compatible authenticators.
What can Secfense product do? How is it built?
The product was designed by a startup from Poland. The company run by Marcin Szary and Tomasz Kowalski offers a solution that helps protect end users by introducing any two-factor authentication method into a web-based application without changing its code or database – within minutes, not weeks.
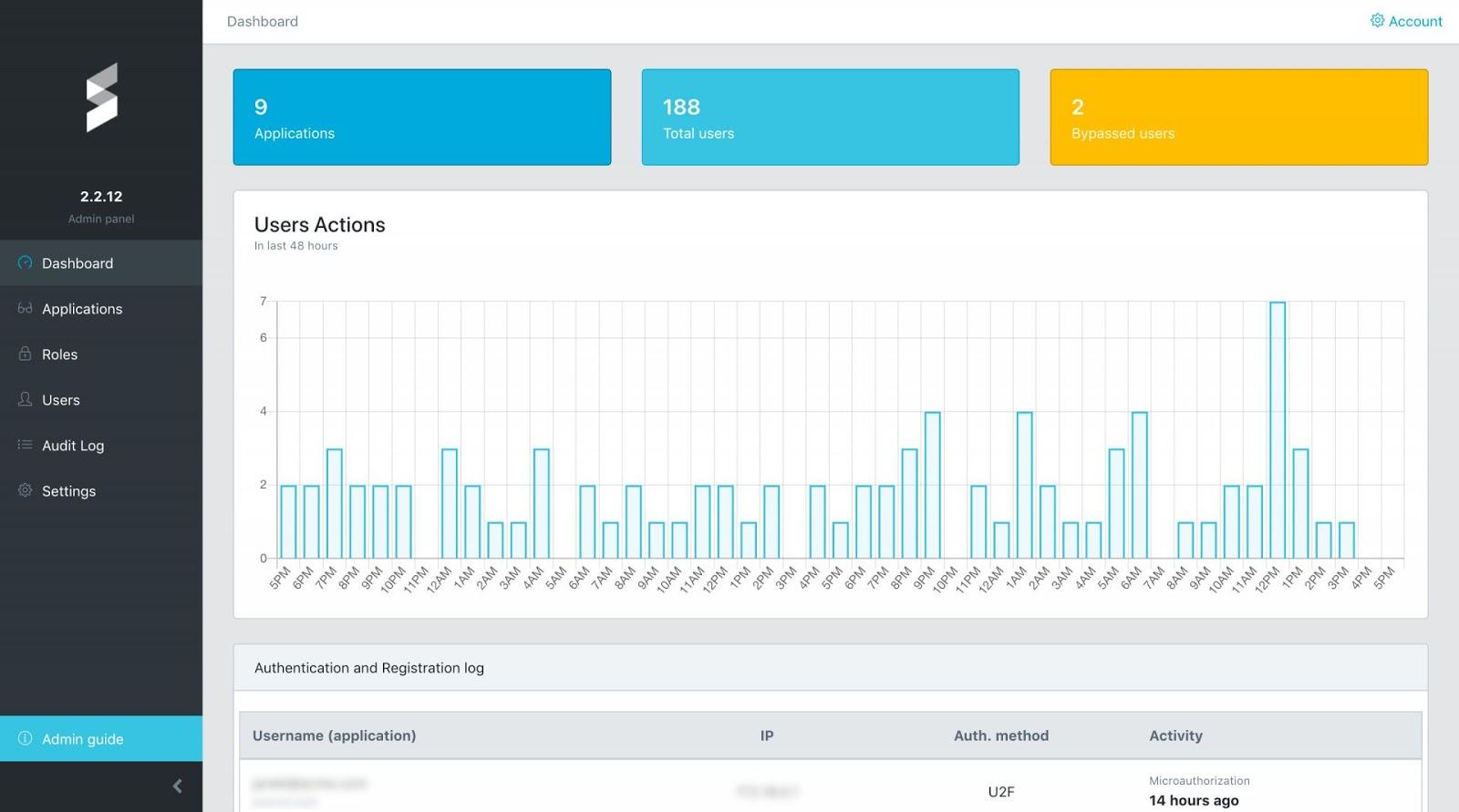
In one box, Secfense consolidates known authentication methods. The solution works as a reverse proxy, which is located between any application and the user. It learns authentication traffic patterns and appropriately enforces the login method set by the administrator.
Secfense UASB does not interfere with any application located in a container, public cloud or data center. An internal application or public Internet resource does not even need to have a 2FA implementation. Secfense creates a layer with the message that you must log in.
Can Secfense replace the VPN in the organization?
A password-protected VPN is not secure. It is also difficult to prejudge that, according to the zero-trust model, no stranger should be in the organization’s network. Instead, it’s better to implement strong authentication. Secfense UASB does not have to replace VPN, as it can support login via SSL-VPN, establishing an additional layer of security. The product will not allow unauthorized users to access the IT resource.
Secfense UASB does not store passwords or process them in any way. The target application’s authentication remains unchanged. The solution simply adds another login layer based on TOTP codes or asymmetric cryptography.
Logging into websites with the support of methods based on the FIDO standard is currently the safest method. Login security using this method can be narrowed down to a single sentence description. If the hacker does not have physical access to the key, then technically he will not be able to log in – even if he knew the login and password. Attacks known to bypass 2FA will not work on the U2F protocol.
Specific situation: what if a company application or control panel cannot be integrated with 2FA / FIDO technology as an important element of IT infrastructure? No worries. This is what Secfense UASB does – it protects the IT resource with authentication methods supported by its producer.
Advantages of Secfense User Access Security Broker
Using two-factor authentication does not guarantee the security of your online account, but significantly impedes attackers from accessing the application. It is worth using 2FA at least in a form of TOTP software token, which is super convenient, because that the employee always carries smartphone anyway and the appropriate application is free to download and easy to use. Currently, the highest security is guaranteed by the hardware cryptographic security key, which is why Secfense does not prevent you from using any authentication solution. On the contrary, Secfense:
- Works with any two-step verification application.
- Works with any U2F security key that complies with the FIDO standard.
- It makes the organization immune to the whole range of attacks based on phishing, among others client domain hooking.
- Can enforce the user access management policy regardless of the internet service or web-application.
- Implements 2FA where such a login method was previously not possible (eg administrative panels and legacy systems).
- Can monitor and record every login, which increases transparency and hinders attacks from within the organization (counteracts employees working for competition).
- Does not store or process any user passwords.
- Does not send any information to the manufacturer.
- Offers so-called micro-authorizations, which aim to add the next authorization step where it is necessary. Examples of micro-authorization are:
– Google engineer pressing the U2F key button, sending a portion of code for production (eliminating the risk of man-in-the-middle attack).
– Sales employees recording every activity (elimination of data theft by dishonest employees).
– Hospital receptionists with daily access to very sensitive data (potentially an easy point to attack by low IT security awareness). - The manufacturer can implement any method on request (U2F, OTP, biometric authentication) for any application without programming and code interference.
We did not take payment from Secfense for preparing the review. We think that this is a very good product, which brings a lot to the world of data security. For this reason, we issue the “AVLab Recommended” recommendation and encourage business readers to test the full version of Secfense, which has absolutely no impact on the IT infrastructure.
SUMMARY
Producer: Secfense
Name: Secfense
Tested version: For companies
Website: https://secfense.com

The Polish startup Secfense has prospects to become the largest integrator of login mechanisms. Any size company can implement two-factor authentication (2FA) using one-time codes or universal 2nd Factor authentication (U2F) using security keys. Without hiring programmers. Without access to third-party application code. No hidden costs. Fast, easy, cheap and convenient.
The article was originally published in Polish on AVLab portal. The original article can be found here.