CLI Overview
Secfense Broker Command Line Interface is available on port 22 via SSH protocol. Although a wide range of configuration and diagnostic options is available, only a subset is required to properly administer the device and troubleshoot any potential issues.
Some level of Linux knowledge is required to operate the Secfense Broker CLI, as the system is based on the Alma Linux distribution.
This manual focuses on CLI contexts important for the day-to-day operations of Secfense Broker.
Docker Containers
Secfense Broker operates as a set of cooperating Docker containers. These containers vary in their criticality to Broker operations; some failures are acceptable, while issues with critical containers can result in complete system failure. You can list these containers and their basic information using the command docker ps.
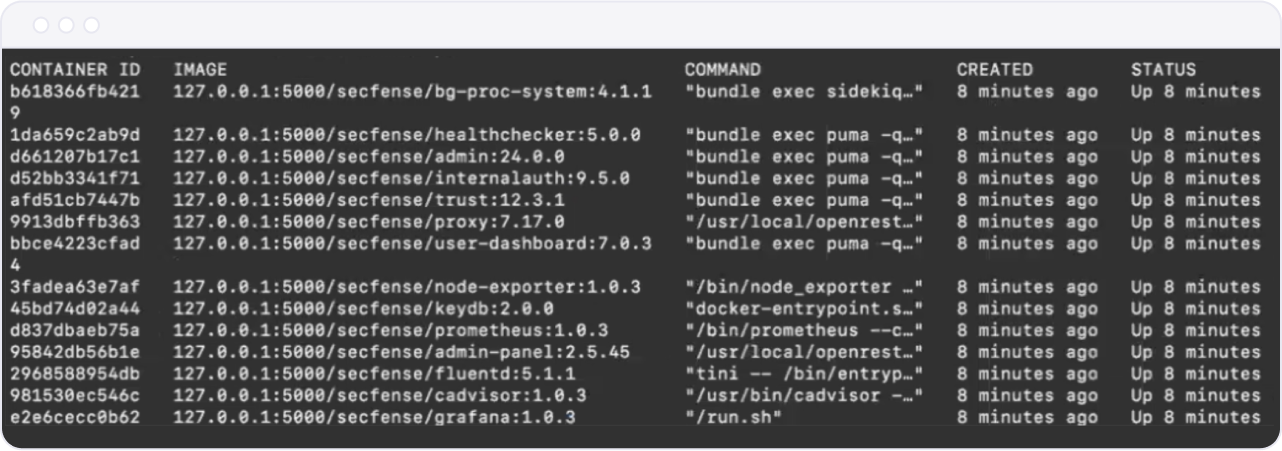
These containers and their purpose are as follows:
bg-proc-system– Handles all background operations—any operation that does not complete within milliseconds is sent to this container for processing.admin– Contains the admin panel API and handles administration functions and procedures.internalauth– Responsible for procedures related to conducting authorizatio- `user-dashboard: Manages user dashboard operations.
healthchecker- Gathers information related to appliance health. This information is usually served from the proxy container. More information about health checks will be in the next section of this manual.trust- Creates trust between users and Secfense Broker. It saves users who have properly enrolled in the Second Factor and successfully logged into the protected application. This container is separate from the user context—no user can directly interact with the trust container.proxy- Responsible for processing and relaying user traffic.keydb- Storage container for Secfense Broker.admin-panel- An Nginx component that serves the REACT application (the admin panel on port 8002). Depending on the context, it further relays traffic to other containers.fluentd- Intercepts and processes the log stream.node-exporter/prometheus/cadvisor/grafana- Responsible for logs and metrics related to system operation.
Administration Scripts
Several administration actions can be performed by specially crafted scripts located in bin directory. These scripts are:
change_ip– Changes the IP address of Secfense Broker.cluster_wizard– Configures a cluster between two Secfense Broker instances.healthcheck– Gathers information about device health. You can view the information (served by the proxy container) using one of two locations:/secfense/healthcheck– A basic health check that returns "OK" when all critical components are working./secfense/check\_components– A more detailed health check that probes the health of all containers and returns a detailed JSON answer:
{"health-check":[{"service":"admin","alive":true},{"service":"admin-panel","alive":true},
{"service":"fluentd","alive":true},{"service":"healthchecker","alive":true},
{"service":"internalauth","alive":true},{"service":"proxy","alive":true},{"service":"trust","alive":true},
{"service":"user-dashboard","alive":true},{"service":"bg-proc-system","alive":false},
{"service":"keydb","alive":true},{"service":"cadvisor","alive":true},{"service":"node-exporter","alive":true},
{"service":"grafana","alive":true},{"service":"prometheus","alive":true},{"service":"\_rsync","alive":true}]}%
module_chronyd– Sets up a new NTP servemodule_debug– Increases the verbosity of logs gathered on the device. It requires two answers – one is related to trust,user_dashboard,admin,internalauthandhealthcheckercontainers, second is for proxy containermodule_fluent_syslogz– Sets up remote syslog servermodule_ui– Exposes the Nomad (container orchestrator) UI to port 14646. Use with extreme care and vigilance.prepare_support_pack– repares a full support package for troubleshooting. The package is crafted to exclude personal data, keys, and passwords. This can be done using the GUI, but CLI is also possible. The command must be executed with a parameter (file name), and the package is saved as a tar.gz file in the secfense/jobs directory.update_infrastructure– Commits any changes made manually to Nomad (Container orchestrator) definitions.upgrade– Commits the upgrader package. The upgrader container is updated each time a new software version is uploaded to the device. This script levels the environment and prepares it for an upgrade. This procedure is done automatically when an upgrade is initiated from the GUI. Depreciated in versions 15.3.5 and newer.vrrp_wizard– Enables and configures Virtual Router Redundancy Protocol between two clusered nodes
Log collectors
Administrators can navigate to the folder /var/log/containers to find files containing the latest entries in the log files. Rotated files have dates appended to them, while the current log is in the file with no appendix. Each container runs its own log file with the .log extension.
Two log collectors of particular interest to Secfense Broker administrators are:
- proxy.log: Contains logs related to network traffic.
- internalauth.log: Contains logs related to particular authentication sessions.
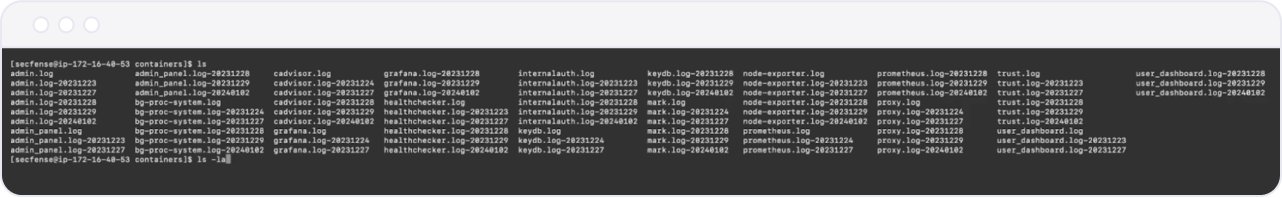
Log files are rotated daily and last for 5 iterations according to the logrotate definition:
/var/log/containers/*.log {
missingok
notifempty
rotate 5
daily
sharedscripts
postrotate
/usr/bin/systemctl kill -s HUP rsyslog.service >/dev/null 2>&1 || true
endscript
}
Secfense health checks
The healthchecker container serves two levels of healthchecks via HTTP protocol:
- basic healthcheck – Served under
http://secfense_ip/secfense/healthcheck. It returns "OK" when all critical components are working - component healthcheck – Served under
http://secfense_ip/secfense/check_components. It returns detailed information (alive: true/false) for every Broker component:
{"health-check":[
{"service":"admin","alive":true},
{"service":"admin-panel","alive":true},
{"service":"fluentd","alive":true},
{"service":"healthchecker","alive":true},
{"service":"internalauth","alive":true},
{"service":"proxy","alive":true},
{"service":"trust","alive":true},
{"service":"user-dashboard","alive":true},
{"service":"bg-proc-system","alive":false},
{"service":"keydb","alive":true},
{"service":"cadvisor","alive":true},
{"service":"node-exporter","alive":true},
{"service":"grafana","alive":true},
{"service":"prometheus","alive":true},
{"service":"\rsync","alive":true}]}%
Both health checks can be used, for example, to monitor Secfense Broker in monitoring tools or load balancer health checking scenarios by using the appropriate URLs.
Application Representation config files
All application representation configurations are held (as separate files) in this location:
/secfense/app/shared/configs/<application_name>