What’s the story?
Hello folks. I’m Christiaan Product Manager at Google working on Identity Security features, and I’m going to talk about authentication best practices at Google today.
Bit of a spoiler. It’s going to be kind of security key heavy. So if you don’t know about security keys already, after the session, hopefully, you’ll be completely skilled up. If you don’t like security keys, I guess you should leave. – Christiaan joked – Hopefully I’ll convince you. So anyway, let’s get started.
With these words, Christiaan Brand, Google Security Manager, started his talk during Cloud Next ’18, the annual Google conference where Google managers explore the latest trends and technologies with a broader audience.
Before you continue reading this pretty long blog post here’s a disclaimer. This article is heavily based on Christiaan Brand’s speech from the 2018 Cloud Next event. If you have 30 minutes you can also watch his video and basically, you will learn the same thing.
The first reason to write this article was to give people, who don’t have 30 minutes to spend, a chance to briefly scan through the text and find the info that is especially interesting to them.
The second thing is that the philosophy behind Christian’s talk is just perfectly in line with what we do and we fully identify ourselves with that. So the way of thinking that Google proposed and introduced for all their employees to protect them against phishing and credential theft is what we are now is also the way that we pursue with our customers to protect their businesses.
You’re cool with that? OK, then keep reading!
What’s your password?
So let’s start with this statement – we at Google don’t like passwords and if you’re not convinced already, hopefully, the next couple of slides here will convince you why we don’t like them. If you’ve seen my presentations before you will recognize these things.
At this point, the audience was presented the two most often used passwords of 2015: 123456 and password.
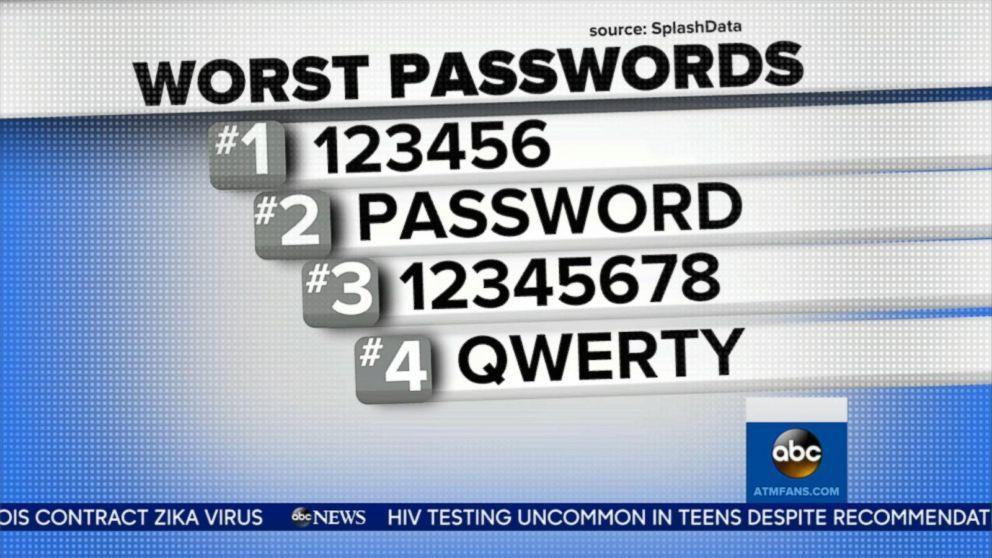
In the early 2000s no one would probably be surprised to see that, but in 2015, when cybersecurity awareness grows and every week there’s a new scandal about the cybersecurity breach, people losing money, and companies losing credibility you could have thought that people are slowly starting to learn their lesson. But apparently, we’re still far from it.
In 2018 two most popular passwords are 123456789 and qwerty. Not much has changed during these three years, isn’t it?
Even though that one in 61 emails in your inbox now contains a malicious link.
Even though in 2018 phishing attacks increased 250% compared to the previous year.
Even though since 2015 cyber-attacks bring more money than the drug trade.
In spite of all these worrying statistics, people still seem to be pretty relaxed when it comes to their data security.
What is two-factor authentication?
Christiaan continued with his speech.
We did a study and we found that about one in two people falls for sophisticated phishing emails. If the email is well crafted one in two people will fall for it.
I know there are lots of vendors doing a wonderful job trying to educate users to scrutinize the website, the URL, the email and hover over it and lots of stuff.
The fact of the matter is… that’s a hard problem.And it’s not much better at Google… We really had to innovate to try and solve this problem. About 76 percent of security breaches last year were due to weak or stolen passwords in some way shape or form.
So that was the opening part. Even though the audience was pretty technical seeing all these facts and numbers really made some impression and woke up the audience that was already in a snooze mode after the whole day of other presentations on a panel.
Christiaan moved on from signalizing the problem to describing possible solutions. Many companies on the market for years now have been using a thing called 2FA or MFA (which stands for two-factor authentication or multi-factor authentication). This method basically requires a user to have an additional attribute apart from the password with which he or she can confirm his identity. The most popular methods used by banks and big companies are text-based messages (SMS) or generated with physical tokens one-time-passwords (OTPs).
This method, however, even though that is much better than protecting resources with a password only still leaves just too much to wish for. It has been breached many times and for a medium-skilled hacker breaking OTPs is not a big problem anymore.
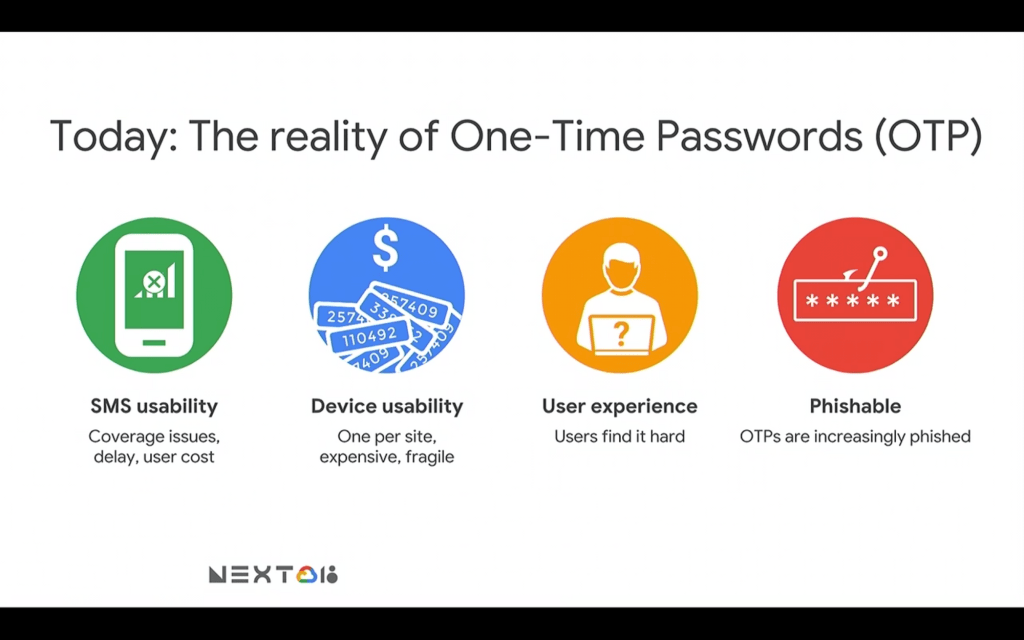
And while OTPs are successful against things like password reuse they really don’t solve fundamental problems.
First, of course, there are usability issues.
You may have seen that in Wolf of Wall Street. Where the character had to walk around with a necklace of tokens around his neck. About 20 or 30 of them on a chain because, to securely authenticate, you had to have a different key for each service.
So not that great user experience.

You have to look at this one thing that generates a code and then type stuff on a keyboard. That’s really like 2009, we don’t really want to do that anymore.
So that’s why the industry has innovated and has come up with other solutions – things like push-based authentication, which is great from a user experience perspective. You’re on one device. You get a message you click a button you’re signed.
But fundamentally, all of these technologies are still phishable.
Ultimately if you have someone, a man-in-the-middle sitting between you and the real service, you can be tricked into not only revealing your password but also your one-time password and also potentially saying yes on your phone to the wrong login attempt.
That was the moment when Christiaan showed a scenario where a successful phishing attack is concluded on an app protected with a 2FA. I recommend hopping to a video to see step by step how easily such fraud could be performed on an incautious user.
Why phishing attacks are getting more frequent?
Phishing attacks are and will be growing because it is and will be the easiest, fastest and cheapest way to compromise companies. It’s much easier to create a technology with some good filters that don’t get fooled by a phishing attack. It’s much more difficult to train an employee not to fall victim to a well-orchestrated and socially engineered phishing scam.
In 2018, for example, so-called ‘whaling’ attacks (where the victim is a C-level executive) have risen 200% compared to the previous year.
And while c-level attacks usually take months of preparation and a lot of work from a hacker, there are still low-level employees that are much easier to trick, and the gain may be surprisingly high as well.
Data shows that it’s enough to gain access to a few standard accounts or one admin account to compromise the entire organization.
So normally if I want to sign in somewhere, what do you do?
I start by going to the website, typing in a password, sending it to a server and at that point, I’m logged in.
That’s pretty much how authentication works.
So at Google, we want to eventually replace passwords, but to get there we first want to simply make the password safer.
What is the U2F security key?
The idea behind the Universal Second Factor (U2F) key is that you have your password you have the second line of defense, which is your security key. And only then can you actually get to your account data. The description sounds exactly like 2FA because, in fact, a security key is one of the methods of two-factor authentication. The difference is that here you need to have an actual physical object built exactly to serve that one purpose – safe authentication.
The security key is a device based on asymmetric cryptography. A physical object that you can physically connect or insert to your computer or cell phone using USB, NFC, or Bluetooth. And it’s this local connection that gives physical security keys the added advantage over other types of two-factor authentication technologies.
Why is U2F Security Key so different?
Essentially security key comes stateless out of the factory.
It’s blank – there’s nothing on it. When you want to use it you would need to go and register it with a specific account.
So for example, to register it with a Gmail account, what really happens is that this device generates a public-private key asymmetric keeper. The private key is kept secure on a device and the public key goes to Gmail.
And at the point in time where you want to sign in, it’s a simple cryptographic signature that this device then generates.
The thing that makes the private key so unique and secure is never actually revealed to the server.
So even if there is a breach with password database is being compromised, security keys are immune to that type of attacks because the secret, the thing that makes the security key able to prove that this is your security key, never actually leaves the device.
The fact that the password leaks all the time is nothing new. A good way to check, not if, but how many times your password has leaked is by going to a page called https://haveibeenpwned.com/ and finding it out yourself.
At the moment of writing this story, there are more 1.9 billion stolen passwords and usernames available on the black market, and up to 25% of them will still work on a Google account.
But going back to the security key itself and Christiaan’s speech on it.
What is FIDO Alliance?
The coolest part of this is that it is, in fact, one device – many services. In the past, you had to have a separate key for each service and you had to go around with a necklace of keys. The idea here is that there’s a lot of services apart from Google that you can associate with this key.
There is Facebook, Salesforce, Dropbox, Github and I think we’re going to see even more services that support Fido Alliance and web security keys with time.
If you visit this website you will find all the companies that have already joined the FIDO Alliance and by doing that enabled security key-based two-factor authentication for their users. It’s really worth taking time now and click the link and checking which of the brands that you’re using every day (like for example social media) enables security key protected two-factor authentication.

Whenever you register your security key with some service it’s privacy-preserving in a way that none of these services can tell that you are using the same security key for other apps.
You can register your key with Facebook and with Amazon for example. Even if Facebook and Amazon would like to collude on the back- they would not be able to tell you are the same user that uses this key to authenticate on any other app.
How expensive are the U2F Security Keys?
At the time of writing this story in early 2019, these keys are moderately expensive. You can get them online from like 20 up to $50 depending on what brand and what type of key you buy.
But the point is that you only really need one key (or probably more reasonable two, as a backup), but you don’t need a separate key per service, which is used to be a struggle in the past with security tokens and which is a big relief here.

How do security keys work?
Here again, I would advise you to click the video and see the step-by-step walkthrough that Christiaan gives. If you prefer the brief, text version though here it goes.
A physical security key (usually in a form of a black, blue, or gray small plastic device), has a virtual key encrypted on its inside called a private key.
When the key gets registered within the application it is supposed to protect it generated two virtual keys. A private key and a public key.
These two are mathematically linked.
The public key then gets into the server. The server now knows something about the key that you’re supposed to present during authentication.
Next, you need to send your password normally do, but in addition to the password the security key now also proves that it’s there really to the server. And the way that it proves this is very simple.
Firstly, it tells the server ‘I promised a user was actually present during a login’.
But how is that done?
Well, all these security keys have a little button on them. And that little button, when clicked, tells the remote server that there was physically a user present at the point in time where this authentication was happening. Why? Because someone had to press the button on the key.
The next stage is a server challenge which is a pretty straightforward thing.
It makes sure that we can’t just replay authentication attempts. So every time you sign in the server will send a new random challenge to the key. And the key has to echo that back to the server.
The thing that comes next is what makes security keys so different from other two-factor authentication methods.
The security key also echoes back to the server the origin or the web property that the user is on when authentication is happening. And that’s what makes it unique and resistant to phishing. Because when you’re trying to sign in this security key needs to tell the server that this is protected application’s property that you are trying to access at this point, and if it’s not, the server will simply not accept the response that is coming from the security key.
You might say, well if there’s a bad guy in the middle then he can just change that. Well, they can’t because what’s important here is that that whole yellow block there is digitally signed using this private key that’s inside the security key and the server can recognize that by decrypting it with the public key that it has for this specific security key for this relationship. So that’s kind of part of the magic.
How do security keys help defeat phishing?
Again at this stage, I recommend you to stop reading for a moment and just check the original video so you could see how the phishing attack is performed and how exactly does the security key protects a user against that.
Google has introduced these keys and as reported in Brian Krebs’s articles, Google employees see no password phishing or account takeover because of these security keys. First introducing them and then making them mandatory for Google employees to use, was what changed the situation completely. Now, you simply cannot log in to a system without a security key.
That’s how we make sure that our employees don’t get phished.
Not by telling them not to get phished, not by sending them emails or putting them through training.
You can do all of that and it’s great.
But in the end, it doesn’t really work, security keys are the way to really get that level of protection.
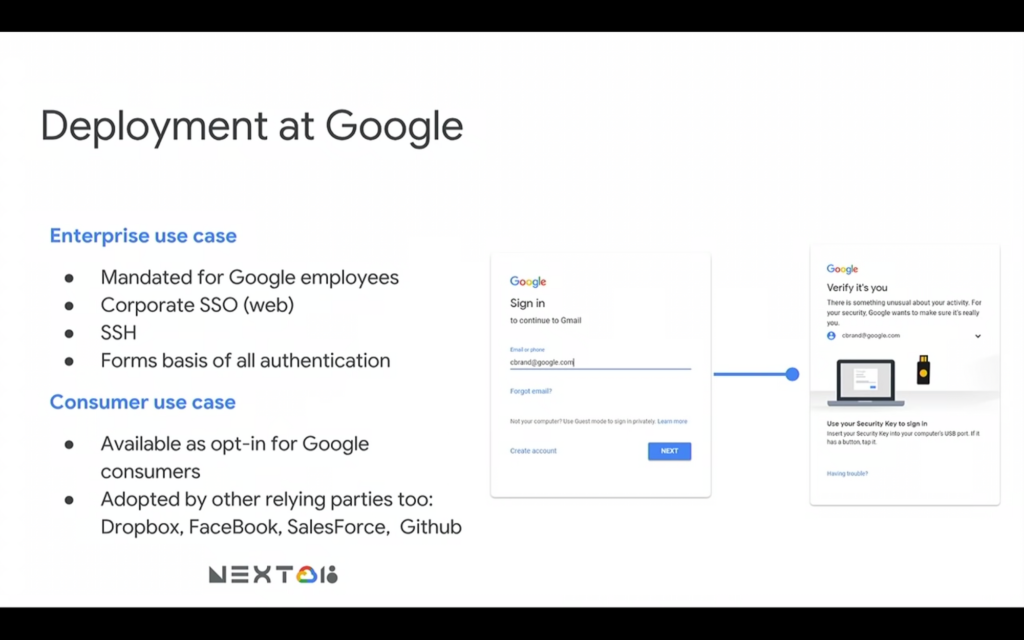
Can I use a security key for my personal stuff?
Yes, at the time of writing this story Google is running the so-called Advanced Protection Program which is designed for people who feel that due to their activity and work they may be at greater risk of their data being compromised. In one of their ads Google lists:
If you’re an activist, journalist, executive, thought leader, a public official or part of the campaign team.
Or anyone that feels vulnerable to highly targeted online attacks.
Google Advanced Protection Program is our strongest level of account security and is designed for you.
Is security key only for my Google Account?
No, it’s been adopted by other relying parties as well.
It’s not only a Google thing.
It is a worldwide thing.
It’s a standard thing adopted by Dropbox, Facebook Salesforce, Github, and a whole lot more. Basically, if the account that you would like to get extra protected is hosted by one of the brands that belong to the previously mentioned Fido Alliance then it means that you can use a security key on it. And it doesn’t matter if you are going to use Feitian key, Yubico key, or Titan key (branded by Google).
All these keys are U2F (universal second factor) so all of them work in exactly the same way.
Why security keys are better than other 2FA methods?
1. They are faster to use
So let’s quickly look at some statistics here that we’ve seen a Google.
First thing is that it’s simply way easier to use than other types of two-factor authentication. The slide below shows how much time does it take to authenticate using a security key (which you basically need to tap and that’s it) versus OTP based method like a text message sent to your phone or a code generated by an authentication app.
SMS-based authentication takes almost three times and application-based authentication takes almost two times as much as authentication with a security key.
It’s pretty obvious because with a security key the only thing you have to do is to take it out of your pocket and press the button. Very easy, very straightforward.
OTPs just took a long time because you have first to type the code.
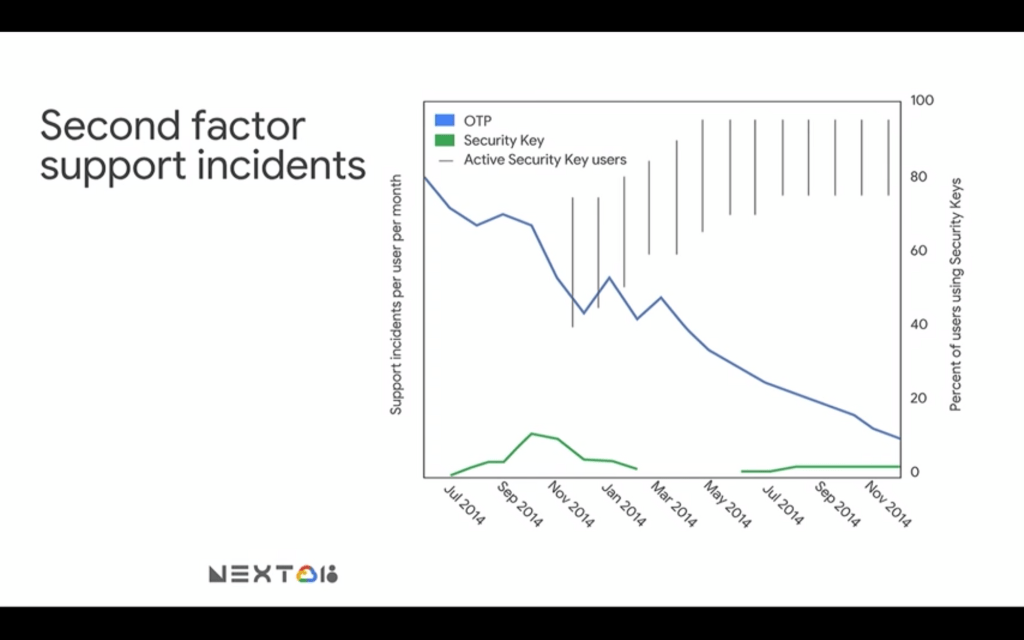
2. There are fewer support incidents
The second advantage is less obvious and is related to the second-factor support incidents.
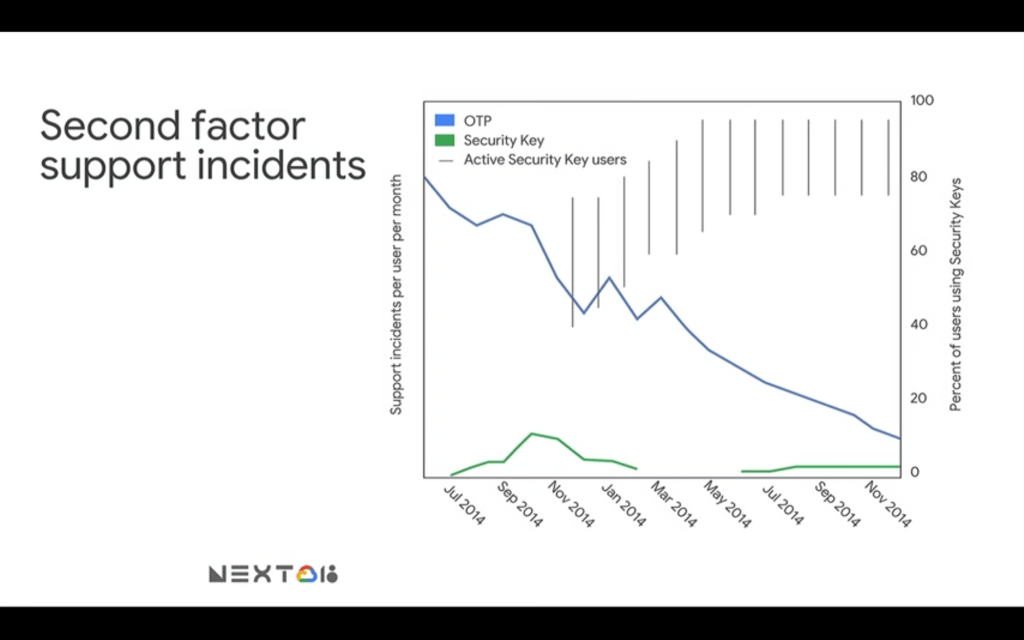
To decrypt the slide above a little bit Google had a whole bunch of support incidents when they first started it. The bottom x-axis is a timeline showing the deployment of security keys.
Now, the blue line shows the number of incidents related to OTP methods, and the green one shows the incidents connected with security keys. The reason why the blue line goes down so fast was caused basically by the fact that security keys have been introduced in November 2014 and since then more and more Google employees have been shifting towards using them until the year later when they became mandatory to use.
Security Keys cause fewer support incidents than OTPs and support incidents directly equate money. So you can save money by deploying security keys.
Security keys play an important role in the BeyondCorp story
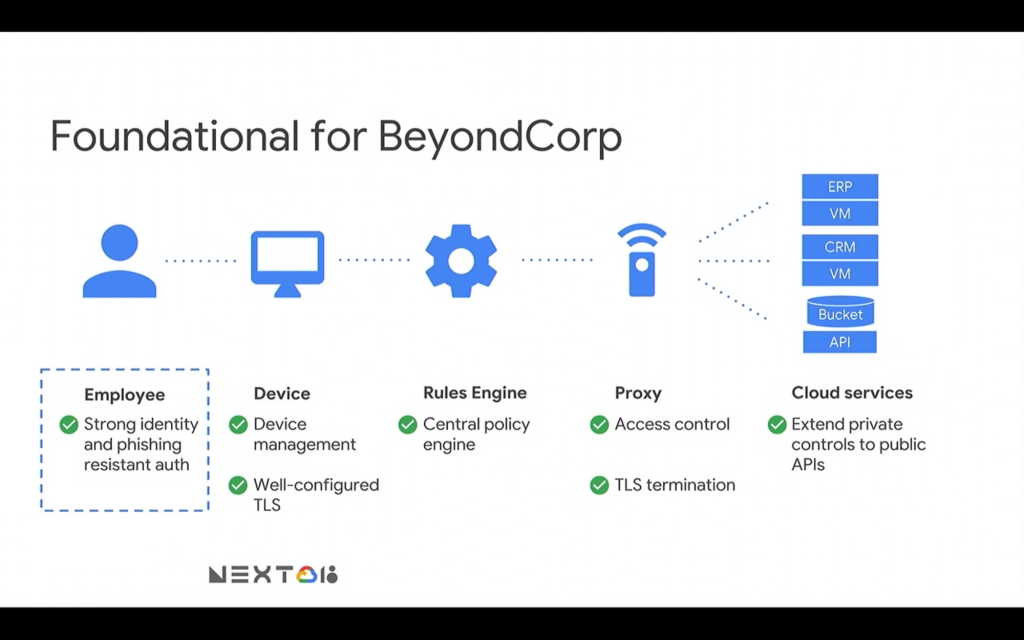
Google’s BeyondCorp is a distinctive way of thinking about corporate security. It basically sums up to things like:
Google’s BeyondCorp:
- moving away from VPN
- not trusting the network across the endpoints
- proving your identity with a security key
So deploying security keys is really the single most important thing that you can do to protect your data. We definitely think if you’re an admin you should use a security key, users who have access to change things in production, who access PPI, those are the user for whom security keys are imperative.
Do all the people in my organization should use security keys?
Probably not.
In Google, that’s the case, but also, Google is a pretty special case.
It makes sense to first review your employee roles and then decide who deals with what kind of responsibilities and what kind of risk is related to that specific role being compromised.
There are two axis of configuration in which an admin can set up security keys. It’s possible to pick on which users should enable security keys and also, more importantly, it’s possible to enforce the use of security keys on some users.
Employees that belong to this group or an organizational unit will need to have a security key always with them to access their resources.
The standard procedure for Google employees looks as follows.
- The admin gives a user seven days to comply with the security policy
- The admin sends to an employee all security keys and asks him or her to set them up.
- If after seven days that employee still has not set up a security key he or she will not be able to log into an account and all other two factor methods will disappear. There will be no other options than to use a security key and hence, contact the admin.
That’s the best level of protection that you can get.
This obviously might not be a necessary policy for every user in the organization so it’s up to the security team to decide on which level enforce on whom.
Maybe it’s ok to access the company mailbox without the key but to access production resources or run some APIs, then that’s the moment to authenticate with the key?
If you’ve ever seen a Google worker on a laptop somewhere probably seen them with the security key that’s like semi-permanently built-in or bolted onto their machine and touching it once a day.
The final takeaways
- Passwords are not secure and are easily hackable
- 2FA (two-factor authentication) is the next step to protect your data
- U2F (universal second factor) is the best battle-tested tool against phishing
I think it is the best take away from this session. If you’re a consumer consider using Google Advanced Protection. Consumers that are at risk can consider signing yourself up.
If you’re a CISO, a person responsible for the company’s cybersecurity, or you’re a CEO, a founder and you’re thinking how can you protect your resources with the safest method possible consider introducing security keys to your organization.
How to enable security keys without software development?
As we got to the end of the speech and the end of this article it’s worth reminding why this article is published on our blog anyway?
At Secfense we are strong enthusiasts of U2F security keys and we agree with Christian and Google’s vision to introduce them to the applications that require a higher level of security.
Our focus is on easy implementation of U2F (but also any other 2FA method available on the market including OTP, biometric authentication, face and voice recognition, etc.) without software development and playing with the code.
What does it mean that software development is not necessary?
It basically means that you don’t need to care about:
- production schedule
- vendor/ application restrictions
- work overload
- hiring external software vendor
- or dedicating your developers to new projects
It is possible to introduce any 2FA authentication method on any app by introducing Secfense User Access Security Broker that works as a security layer completely independent of the protected app.
And since the method is independent of the application it can be easily scaled to all the apps in your organization.
That’s how easy it can be.
You can contact us and we will tell you how can we introduce strong authentication in a form of U2F or any other 2FA method within your organization.