Adding 2FA to any web application
Most system administrators don’t like changes. Apparently, project managers hate them. Changes last a long time, rarely go smoothly, and usually generate problems. But it turns out that some changes can help fix security issues in a fast and smart way.
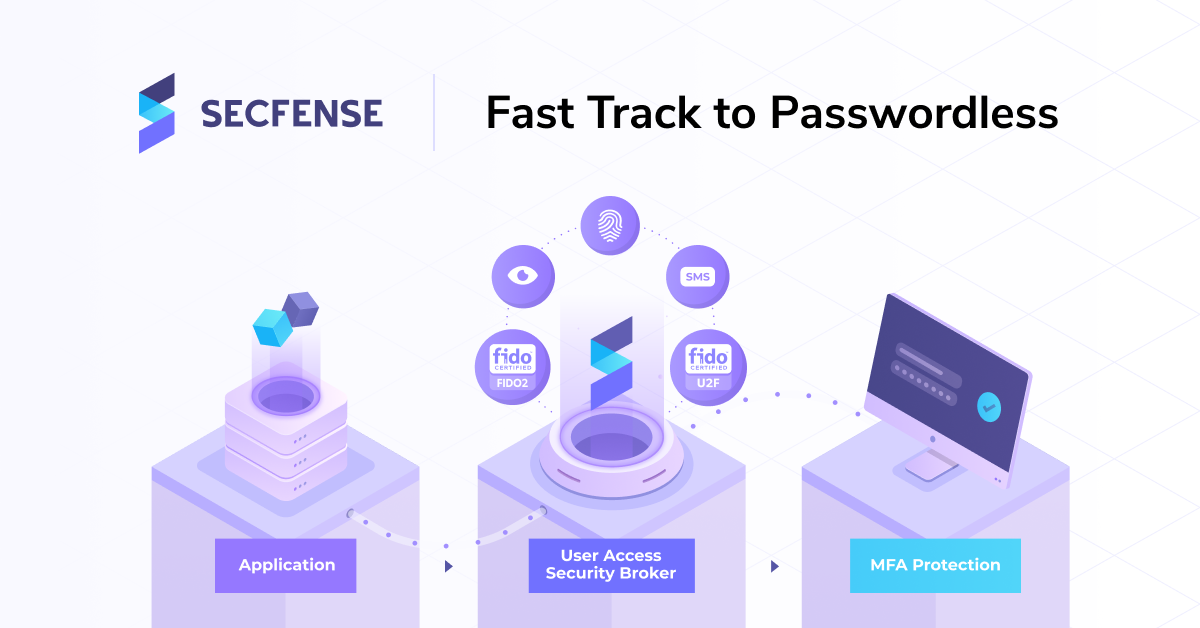
When we heard that someone was proposing a solution to add two-factor authentication to any web application in minutes, not weeks, we didn’t believe it. Then we saw it with our own eyes and we had to verify our views on what can be done in the field of authentication security.
Adam Haertle | Trusted Third Party
Meet Secfense. On Thursday, April 9 Adam Haertle from Trusted Third Party cybersecurity portal held a webinar with Secfense that was recorded (in Polish) and published on Youtube. So if you have 15-minutes (that’s how long the demo part of the webinar takes) you can see it on your own.
An additional layer of authentication without interfering with the application code
There is an application within the company… or actually 150 of them. Yesterday they were only available on the local network, since the COVID19 outbreak half of the Internet may try to access them. Until just recently, a login and password were sufficient, now, with the majority of people working remotely, at least some of the apps require implementing additional authentication. At the very thought of it, everyone’s getting a bit stressed and anxious. From the CIO to the junior programmer and testers. Meanwhile, you can do it quickly, simply and with no sweat.
And this is not just a slogan. If you have 6 minutes, you can watch a live demonstration of how Secfense User Access Security Broker adds two-factor authentication to Amazon.com (important disclaimer: it works on Amazon only for the sake of the demo, normally Secfense needs to be installed within the organization, but the deployment looks exactly the same as shown on Amazon example).
However, if you do not have 6 minutes (because you have to introduce 20 changes into the application in the meanwhile), then, in short, it works as follows:
- insert a properly configured proxy into the application traffic,
- listen to the application ‘talking’,
- define new authentication rules,
- run Secfense,
- that’s it. 2FA is enabled.
And now something even more interesting
If the implementation of 2FA to the application within 15-minutes does not impress you enough, how about implementing an additional layer of authentication for specific operations in the application, without modifying its code?
The Secfense solution also makes such tricks easy.
This time the movie has 1.5 minutes and it explains that you can add the so-called microauthorizations, i.e. 2FA only for administrators or only for data export operations. The Data Protection Officer likes this!
We talked about all this during our last webinar
The one-and-half-hour-long webinar was held just two days after the initial publication of this article on one of the top 3 cybersecurity portals in Poland and in just two days more than 450 people registered to see this!
The whole recording is available on Youtube in Polish with auto-generated English subtitles. We are aware that auto-translation may be far from perfect that’s why we encourage you to contact us and schedule a demo. During a 30-minute discovery call we can show you how it works (15-minutes) and then during the other 15, we run a quick Q&A and check with you if this type of tool can be useful for your organization. If yes – we schedule a POC (proof of concept) which can be done in your test environment in just one day. If no (we’re not fit for everyone) – we point out other alternatives that you can use instead.
In any way, one of the huge benefits of Secfense User Access Security Broker is the fact that it’s so easy to show, explain and test in any environment.
UPDATE:
Below you will find the webinar agenda with time markers, so you can click on the link and it will take you directly to the part that you’re interested in.
Webinar plan:
1:48 – 23:48
Attack epidemic – what has changed and what hasn’t
Adam Haertle, Z3S
23:48 – 28:45
How to add 2FA to any web application in a 15-minutes
Marcin Szary, Secfense
28:45 – 33:01
The problem with the adoption of the second factor in a unified manner
33:01 – 35:54
How do Secfense address the problem of 2FA adoption and scaling
36:37 – 40:11
How Secfense looks from the inside – solution architecture
40:11 – 51:59
Live implementation of the second factor
51:59 – 58:12
Micro-authorization – adding additional authentication in any area of the protected application
58:12 – 1:14:21
Questions & Answers:
– What about Single sign-on?
– Where is Secfense installed? Where is it in architecture?
– What about Office365 and other SaaS?
– Does Secfense work full offline?
– Does Secfense work when the client has one IP address but many certificates?
– Are application cookies rewritten on the portal and decrypted?
– During the demo, the application resolved the name to the IP address when adding Allegro.pl to the upstream URL. Is this value later fixed or updated?
– Can I add options other than U2F?
– Did the solution have a security audit?
1:14:21 – 1:15:49
FIDO keys and a new standard for network authentication using your own biometric device
1:15:49 – 1:20:44
Attack on 2FA using the Modlishka tool (and why Google has opted out of OTP methods)
1:20:44 – 1:25:50
How WebAuthn works on various devices
Disclaimer: The original story was initially published here on Zaufana Trzecia Strona (Trusted Third Party) on of the biggest cybersecurity news portals in Poland and then translated to English som it could be republished on this blog.