MFA trends and recommendations for 2020
2020 may be a year of MFA’s successive and stable expansion to other platforms. Both individual users and company employees will be able to protect their accounts with strong multi-factor authentication.
Individuals and companies for whom data security is critical will be reaching for cryptographic keys more often. There will be more and more companies offering security keys and authentication apps. In 2019 Google, has followed companies such as Yubico or Feitian and has launched its own security key called Google Titan. Journalists, influencers, politicians, high level managers — all of them will most likely be reaching for better protection based on multi-factor authentication and cryptography-based methods.
Other important factors that will increase the popularity of MFA methods are international directives such as the GDPR or PSD2. Both of them had a significant impact on the security awareness of companies and individual users. As a consequence, e-banking customers in EU are already using strong two-factor authentication (as it was one of the requirements of PSD2 directive).
It is also likely that more and more companies will be looking for ways to protect themselves against the consequences of breaking the GDPR and MFA seems like a natural option. It is especially likely in large e-commerce companies, financial services providers and other large and medium-sized companies, which due to the nature of their business makes them a great target for phishing risks and data frauds.
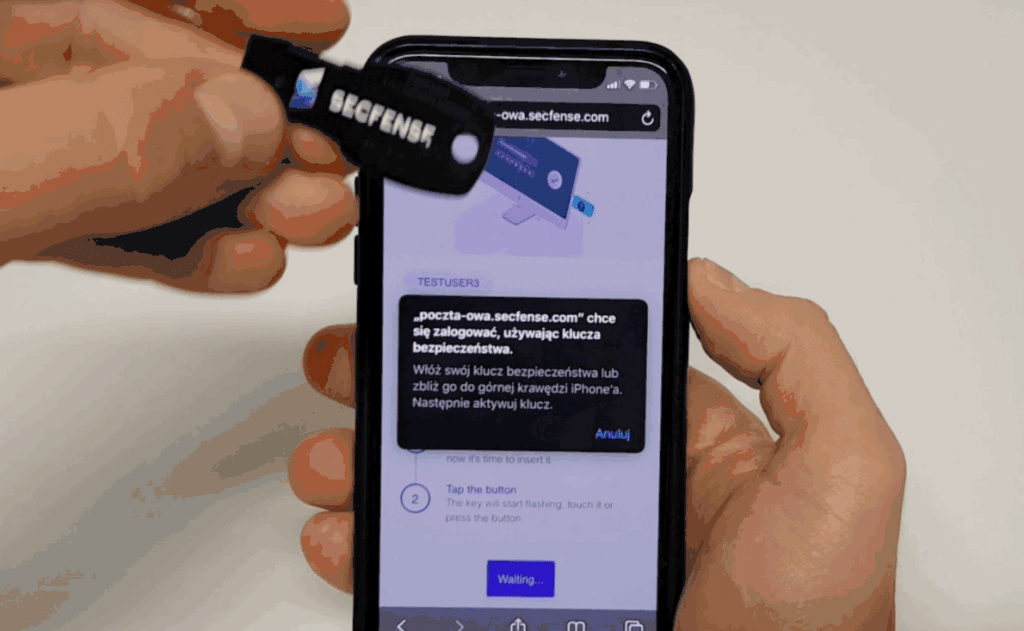
In 2020 the use of local authenticators, may become a particularly interesting trend. We are talking about smartphones with fingerprint sensors and laptops with face recognition, which thanks to the new online authentication standard called FIDO2 (or WebAuthn) can now serve as online authenticators confirming identity on the web.
The FIDO2 authentication standard is something completely new, sanctioned by the W3C consortium only in mid-2019 however the standard will most likely be gaining on popularity really fast. In the last months of 2019 FIDO2 was introduced by brands such as Google, Twitter, Apple or Microsoft and many others.
Recommendations for business
Companies that need to protect their applications with strong authentication should first look for suppliers who will not only enable to implement multi-factor authentication, but also help in scaling it to more applications or shifting from one MFA method to another.
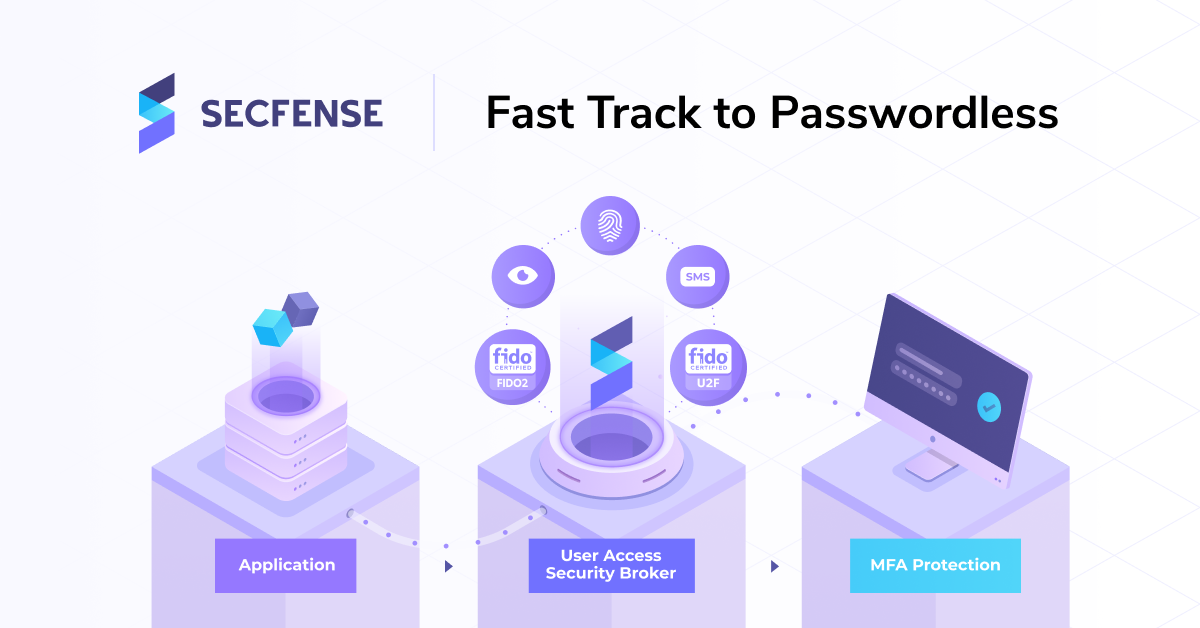
A broker-based approach to authentication seems to be the most desirable. In such an approach, the system administrator is able to easily change the strong authentication method without interfering with the code of an app. System admin can also add MFA to the subsequent applications and subsequent users.
Companies that choose user access security broker based approach give themselves the opportunity to quickly and easily add and adjust a set of MFA methods to their own requirements. In this way, some applications can be protected with a less secure but more convenient authentication app (such as Google Authenticator), and the most critical resources will get protected by FIDO cryptographic keys (such as Yubikey).
What is important to stress out is that the multi-factor authentication broker does not bind the application to one specific MFA method and an authentication method can always be switched to a different one in a few clicks by the system administrator.
In summary, 2020 could be a year of expansion for MFA, as well as a paradigm shift in how the strong authentication method is delivered. Instead of integrating it with the application, it can work independently as a broker without touching the application code therefore avoiding vendor lock-ins and other common limitations.
Read more>>> Strong FIDO2 authentication in applications such as Facebook, Twitter, Google and many others can now be natively used on Apple phones.