Universal 2nd Factor
In 2017 Google introduced little security keys to its all eighty-five thousand employees and thanks to that has completely neutralized phishing. Since then, their employees haven’t reported any account take over.
If you have heard some of our previous talks you will see that we love to start with this story. This time was no different. We got invited to one of the biggest cybersecurity events in Europe called Cybersec Europe. This time we weren’t supposed to pitch our product but rather talk about new trends and universal practices.
So we came and decided to talk about FIDO2 Because there’s simply no better, more important, and breakthrough topic to talk about in cybersecurity in 2019. Period.
Why?
Because it’s a new, open authentication standard that will let you get rid of passwords.
So why if talking about web authentication do we start from Google and their security keys?
Well, because the deployment of these U2F keys (which stands for Universal 2nd Factor) in Google corporation was not only a big thing for that company itself but also a huge step forward for the entire internet security in general. And that step marks the beginning of the web authentication era.
Let’s dig deeper into recent history.
(By the way, you will see us using the name ‘FIDO2’ interchangeably with ‘Webauthn’ and ‘Web Authentication’ as all three mean basically the same thing).
FIDO Alliance and the rise of Web Authentication
In 2013, Google has joined an alliance called FIDO (short for Fast ID Online). That association has already been working on building a standard around public cryptography with the goal of replacing passwords with something better and safer. Google (together with Yubico and NXP) has been working on a pretty similar thing. An open, two-factor authentication standard. So when all mentioned companies joined their forces a lot of progress has been made real quick.
Google has made a lot of contributions to the entire standard. First, they’ve provided the entire specification, the whole blueprint on how things should work. Secondly, they’ve enabled their devices and provided native support of the FIDO standard for Google Chrome and Android OS. This was huge. More than 2 billion devices are instantly ready for the thing. But probably the most important contribution from Google was simply battle testing of this solution on themselves. On their (at that time) eighty-five thousand employees. Such a huge testing sample is a pretty reliable way to check if the experiment is working.
It’s important to mention that Google’s entire infrastructure is not hidden behind any sort of VPN. It is completely open and available on the Internet. Google’s zero-trust security model forces them to change the access controls from the network perimeter to the individual users. In other words, they simply have to have trust in the authentication mechanisms.
Since Google’s experiment in early 2017, the FIDO Alliance has grown in size. Currently, it has around 260 members and is still growing. The alliance includes the biggest names in the tech market. There are companies like Microsoft, Visa, MasterCard, Bank of America, and many more.
The FIDO Alliance
Thanks to all FIDO Alliance members working together on one, open standard, the authentication has become liberated. Now FIDO2/ Webauthn is an umbrella not only for all multi-factor authentication methods built on PKI but also for biometric authenticators that offer a real passwordless experience.
Things have been evolving but the mission of the alliance has remained the same – use local authenticators and public-key cryptography as a means of authenticating users on the web.
The standard is there and it is open. Anyone can produce such second-factor authenticators on their own. Among the biggest brands offering U2F security keys, there is a Swedish company (Yubico), Chinese (Feitian), and the US (Google Titan). You can even build your own security keys because the standard is open and the tools are there.
The security keys belong to a group of roaming authenticators or cross-platform authenticators. This basically means that the same key can be used independently on various devices and can generate and authenticate your identities on the web. The keys have a USB interface and most are also capable of NFC communication over the radio (Bluetooth has been given up due to security considerations).
Passwordless Authentication
U2F keys, while most secure still require you to ‘have them with you while you authenticate. The next group of authenticators lets you get rid of this extra thing to carry around. The authentication uses biometric devices that you already have with you anyway.
Fingerprints sensors or infrared cameras capable of facial verification, all the things that you use now to unlock your smartphones or laptops can now, thanks to FIDO2 / Webauthn, be used to authenticate on the web.
The step-by-step process of authentication is pretty similar regardless of which authenticator you will choose.
- The first step goes like this:
- If you use a USB based security key – you just plug it into your USB port and tap the button
- If you use NFC based security key – you just put it close to your device and tap the button
- If you use biometric reader on your smartphone or laptop – you just put your finger on the sensor and tap the button
- If you use infrared camera on your laptop – you just look at it so the face recognition can work
- In the second step the identity is generated.
- In the third step you repeat tapping from the step one to authenticate…
- and that’s it, you’re in.
How Web Authentication works?
So what really happens here? How the identity is generated and how it is later used in order to authenticate?
During the identity generation, the website (or web application) asks the authenticator to mint a pair of public cryptography-based keys. It’s important to stress that this can only happen after human consent – there’s always a physical action required. Either touching the button, touching the sensor, or looking at the camera. Only then can the public key be released to the service.
After this happens, and a person tries to access the website the randomly generated number is sent across to the public key. And again, after human consent, only this particular key is capable of responding correctly and let the person in.
The other thing that is also important to mention is that everything that has been done happens only within the scope of this particular website. The service is blind to any other identities that were generated by the key. The key could be generating hundreds or thousands of identities, and they will never be cross-linked. Identities that the key generates can never be tracked.
How attacks on 2FA are done?
Earlier in 2019, it was all over the cybersecurity news that 2FA has been breached. That two-factor authentication is not safe anymore and that there are ways to successfully perform an attack on two-factor authentication.
The typical attack on 2FA is a phishing attack with a real-time proxy in between.
The first step is almost always the same. There is an evil actor that tricks the user to click the malicious link. The link takes a person to a fake domain that looks almost like the real service (let’s say bank login site). It usually has some small typo in the name of the site that tricks the person into believing that the website is legit.
The communication between the user and the service that he’s intending to use is real. It’s real-time communication between the person and his bank login site. The only problem is that there is an evil proxy in between. The user is typing his password, and then he’s supposed to give a one-time password generated by his multi-factor authentication app or delivered by a text message to his phone. A person provides the one-time password without suspecting anything and at the same time, the attacker not only intercepts his password but also steals the session. Now the attacker can easily replicate the cookies and replicate the victims’ session. Even though the user authenticated with the second factor he still getting compromised.
Google stopped using TOTP
This is the very reason why Google has abandoned OTP-based 2FA. Initially, they have also been used at Google corporation but since such attack can be done on any OTP/ TOTP based method Google has decided to move away from it.
With FIDO security keys this simply cannot be done. Even if the password gets stolen. Or, like in the previous example, the person will give away the password believing that the website is real, this still won’t permit for the communication to continue. The identity that got generated was generated in the scope of the legitimate domain. So even if the user is really willing to give up his identity to the attacker, there is no way to do it with FIDO.
The FIDO2/ Webauthn, the set of technologies between browsers and authenticators and services is built on three pillars, the three foundations. Security, privacy, and convenience.
Security
means that each identity is securely and cryptographically generated on a device. The identity will never leave the device, will never share any secrets. Unlike the OTP-based method, with FIDO2 there’s nothing to be stolen by the attacker. There’s always human consent necessary, the person has to push the button in order to proceed with their communication. Even if the computer gets infected with malware, there is no way to force the communication without human physical presence.
Privacy
means that identities are isolated. There is no way to track identities across services so we can have the same key or same biometric authenticator protect your social media account, your bank account, and your work-related applications. The information simply never links between one and another. There is also no way to track a user based on the use of his key.
Convenience
means no longer thinking and remembering long and complex passwords. And while there may be debate – what’s more convenient – remembering a password or carrying a physical object? Then this debate doesn’t really make sense when we think of local authenticators like smartphones and laptops. We carry them with us anyway so there’s no extra sacrifice, only benefit. Moving away from passwords and moving forward authentication with your personal devices.
Will all applications use web authentication now?
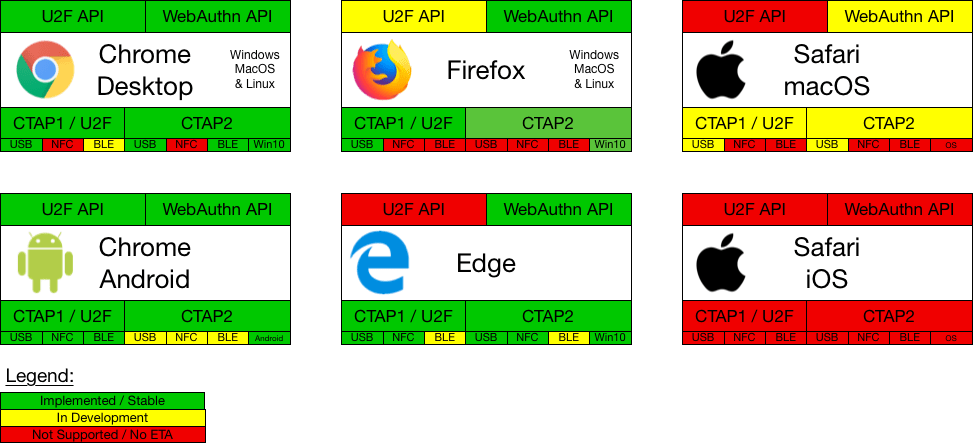
All building blocks are already in place. Tech giants from Silicon Valley have already started upgrading their applications. Many of the customer-facing products are already WebAuthn enabled. At the time of writing this article (November 2019) Chrome, Edge and Firefox have already enabled FIDO2 and Apple started the adaptation of this standard on macOS.
If you are a developer, you can take the specification, upgrade your application and have it done. You can later ask the users of your applications to opt-in so they can do the secure authentication. This is however easier said than done. Not every company has Google’s cybersecurity budget and not every company can take all their apps and redesign them so they all can now use FIDO2 standard. The typical, well-established, mature business has usually hundreds or thousands of web applications and administrative panels that cannot be upgraded just like that. Heavily heterogeneous environments are rarely capable to do a unified change.
This type of big companies usually have only a handful of applications protected by RSA tokens or TOTP-based passwords. Sometimes they use the legacy PKI infrastructure or partially deployed SSO strategy but most of their infrastructure is still left with passwords as a default.
FIDO2 adoption and scaling
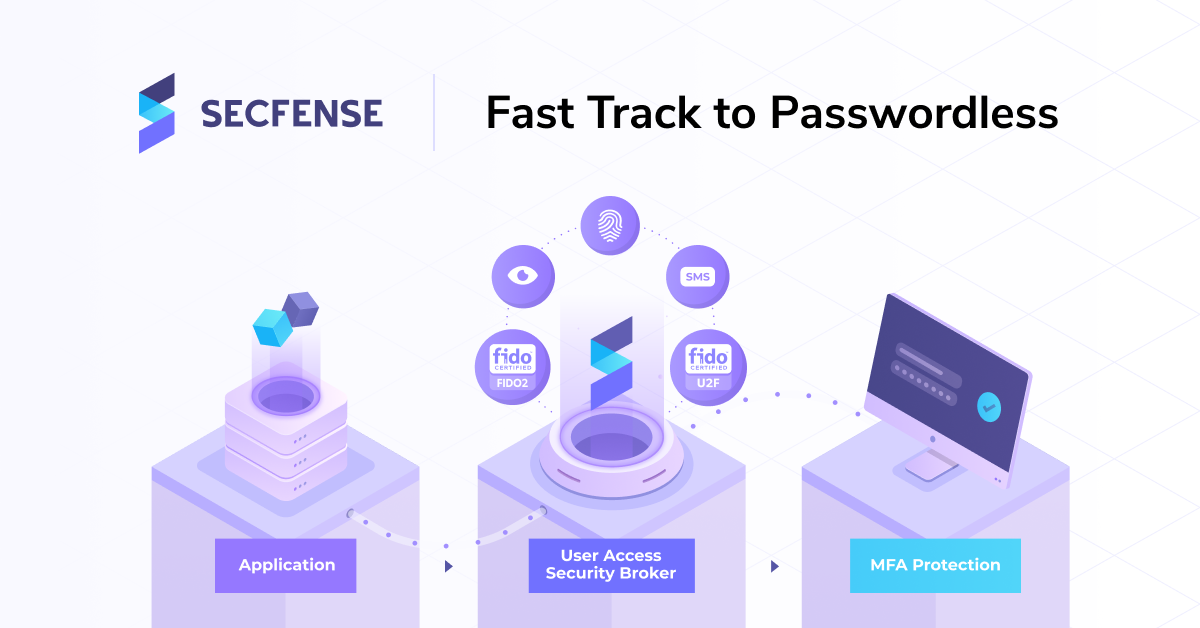
So is there a way to scale web authentication within the entire organization?
The answer is yes. This is something that we’ve developed at Secfense, a technology that can be spread across the organization’s infrastructure and provides things like MFA, WebAuthn, and microauthorizations in transit. There is no need to be updating the applications at all. It doesn’t matter if we’re talking about administrative panels provided by one vendor or custom-tailored applications built internally. We simply do not touch applications’ code. Secfense User Access Security Broker is placed in a position where it simply observes, analyzes, and modifies traffic patterns in order for two-factor authentication to be triggered.
So yes, it’s possible to introduce MFA or FIDO2 in minutes… and since it’s easier to show it live here’s a recording from one of our previous public demos where we have shown how it works.
The tool works as a remote proxy it observes the network traffic, patterns and learns how the application changes on the front-end in the dome.
We can add WebAuthn to any web application in minutes. The integration is no longer a matter of a few months-long project. There is no software development. There is no third-party code that is residing in your applications. And there is no vendor lock-in.
Microauthorizations
Wait, there’s more! Microauthorizations. Being in the position of user access security broker, we have figured out that there is, even more, we can do to add an extra layer of security to organizations. There are certain areas in applications where it’s recommendable to verify if the user of the application is still the same person that logged in to the application initially. That this is not a malware-controlled machine or an automated attack. So we thought we could fix it and introduce a thing called microauthorizations.
How Microauthorizations Work?
are additional authentication steps added to specific segments of the protected application. They are required after the person has logged in to the application. The user that logged in to the app is requested to verify his identity again (in the owner mode) or the authentication needs to be performed by his supervisor (the supervisor mode). Possible uses of microauthorizations are for example:
- a risk of a salesperson stealing contacts from CRM. The risk is prevented by obligatory microauthorization whenever copying/ exporting/ editing sensitive customer data
- a risk of a low-level employee with high-level access to extra sensitive information like receptionists at hospitals or VP assistants. The risk can be prevented by obligatory microauthorization whenever accessing data that is not necessary for an everyday use of that employee.
- software developers sending their code to production and registering batch using microauthorizations. This is actually how Google corporation works, every software developer needs to tap the security key to confirm his identity when sending a new batch.
Microauthorizations Adoption
Same as in the case of MFA and FIDO2, microauthorizations can be added to any web application.
We believe that MFA is becoming a must. Internal security awareness is growing. External regulations like GDPR or PSD2 are becoming a thing. Taking advantage of user access security brokerage can help organizations protect themselves against phishing and credential theft-related risks once and for all.
If you’d like to test out how this solution works in your organization and the proof of concept is very easy and not intrusive. It usually requires just an hour of your network person and if you don’t like it then the rollback is even easier. To learn more ping us on Linkedin and we will be glad to send you more materials or if you prefer to chat you can contact us here.