Multi-Factor Authentication
The market of MFA solutions is completely saturated with a number of solutions and vendors. Just to provide a quick example of how the situation looks like, the web portal called G2 Crowd, which focuses on collecting user reviews for business software, lists more than 140 companies that make MFA software.
When it comes to vendors, some of them focus their efforts on providing comprehensive MFA. Alternatively, there are companies that provide MFA solutions, but have a broader scope and try to offer identity services that cover the management of the whole identity lifecycle.
These Identity and Access Management (IAM) vendors are evaluated every year by Gartner in its Magic Quadrant for Access Management.
There is also a huge range of authenticators that could be used for MFA purposes, offering different assurance characteristics, as shown below.
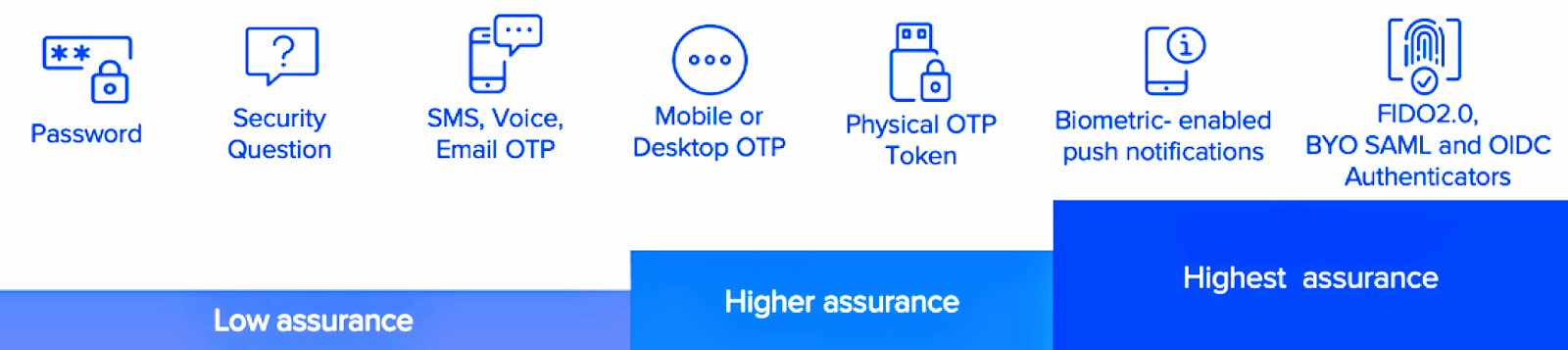
Some of the vendors of MFA solutions, just offer one kind of authenticators (e.g. authentication keys), while other vendors offer a huge range of possibilities (e.g. email, voice call, SMS, authentication keys, mobile push notifications, etc.)
This article will analyze two other possibilities to implement MFA in an organization: Privileged Access Management (PAM) and User Access Security Broker approach.
PAM Vendors
Privilege credential solutions are used in some organizations to protect elevated access and permissions associated with certain accounts.
Generally, an organization that implements PAM uses it for authentication and access management: limit system access and also control the access of authorized users. PAM acts as an intermediary layer, in the authentication process, that allows admins to use their accounts with limited rights for the day to day activities while providing the possibility to escalate those rights whenever it is necessary to perform privilege activities. Here’s an example of a PAM solution:
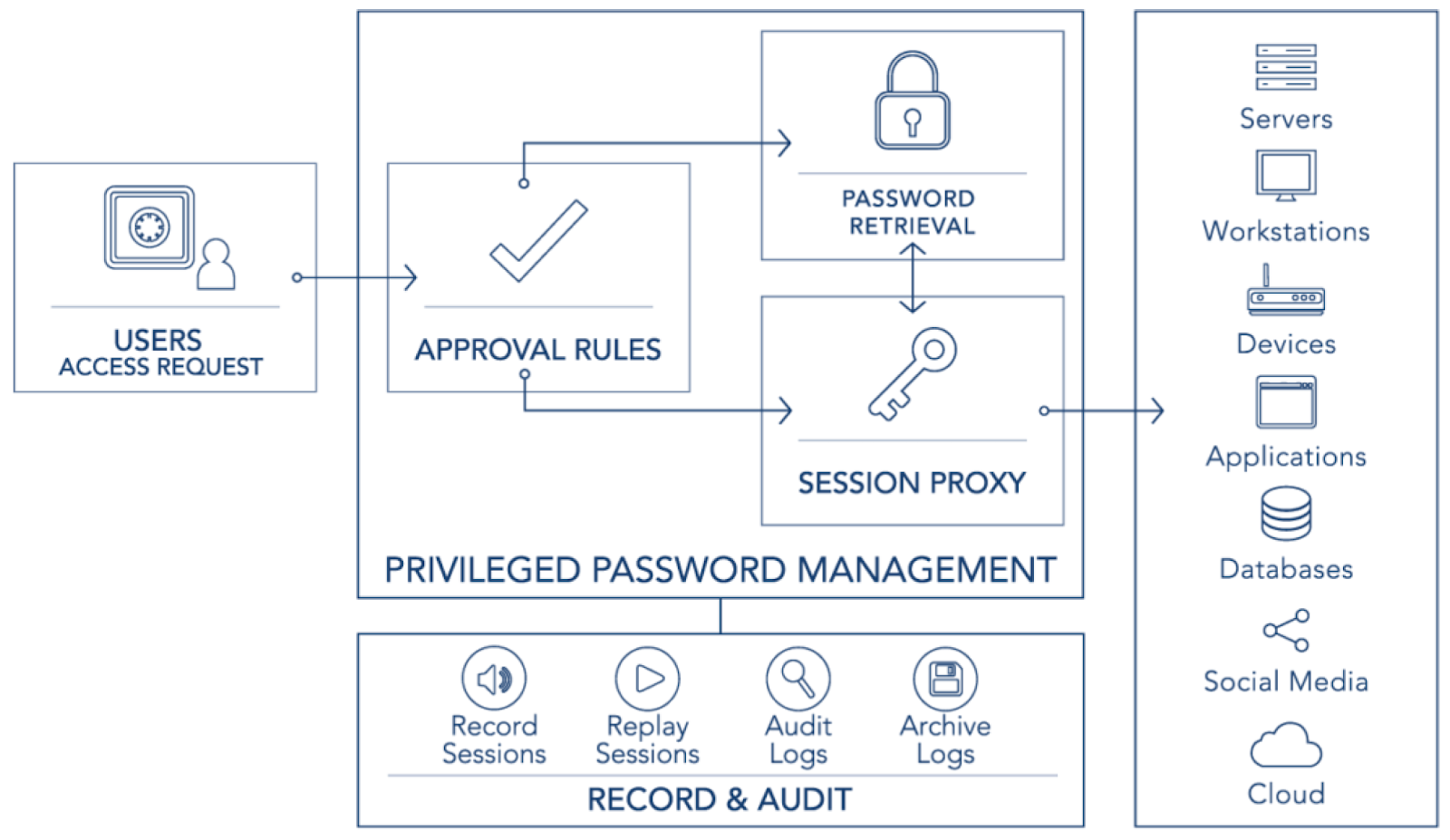
The deployment of a PAM requires the integration of new hardware and software at customer premises. The system sits in the middle of the communications between people, processes, and applications and the different resources that need to be accessed, such as servers, workstations, applications, databases, etc.
The PAM system controls the access to the end resources and will only allow the escalation of privilege to certain accounts and under certain circumstances. This kind of system enforces the use of the least privilege principle and drastically limits the attack surface for internal and external threats, at the same time that offers a centralized log repository where all the actions performed by any account in any system will get registered.
PAM solutions can be combined with MFA in order to provide an extra security layer. Even though it is not very common, PAM systems could be used to deploy MFA in certain systems with strong limitations to integrate with current MFA solution requirements.
User Access Security Broker
The concept of the user access security broker has emerged in 2018 and is on an early awareness stage. It is being tested by early adopters and is slowly getting recognition as a new, interesting alternative to traditional MFA deployment methods.
The added value of this kind of solution resides in the fact that the deployment of only one server, whether it is physical or virtualized, will reduce the number of API integration development that would be necessary for each application, as it is centralized in only one device. The term User Access Security Broker was first used by Secfense to name their approach to MFA adoption and scaling. Below there’s a solution architecture showing where the User Access Security Broker is placed in the company infrastructure.
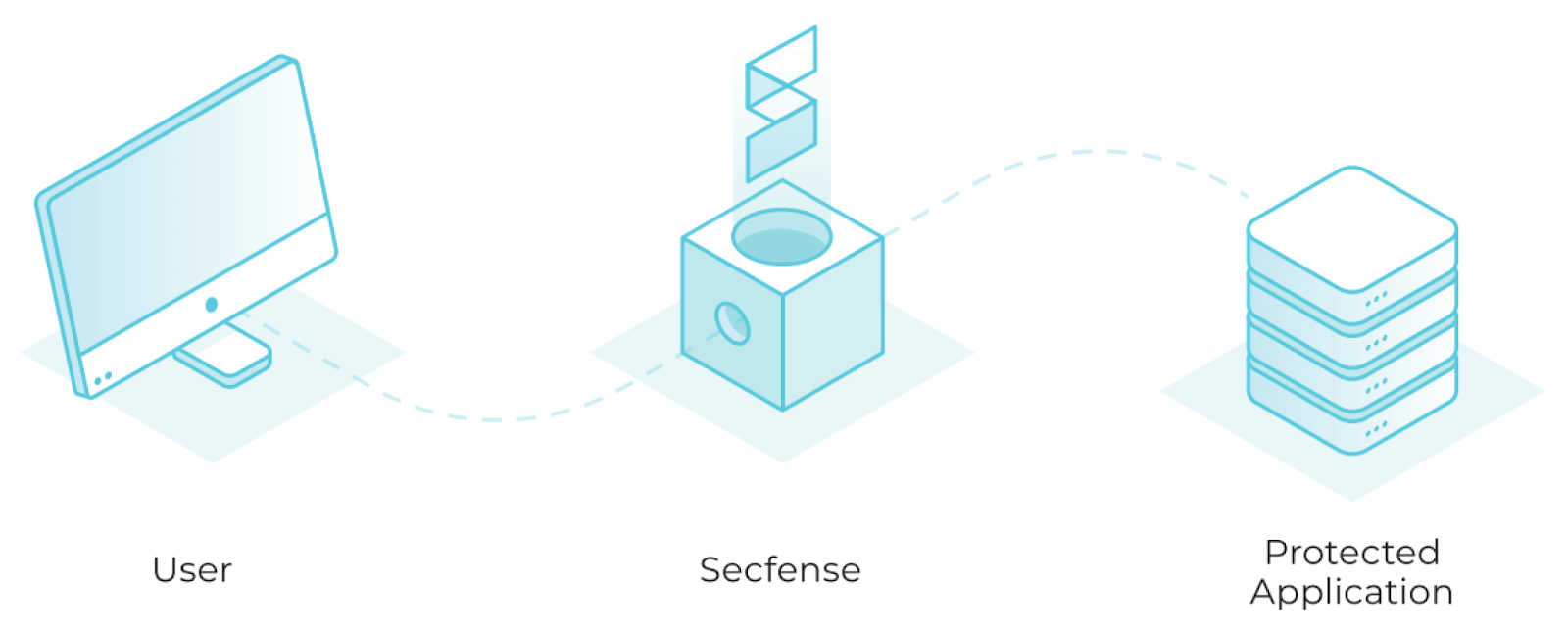
Secfense implementation consists in the introduction of a proxy server in the organization network that will handle user login attempts. The traffic of the organization’s network needs to be diverted to the Secfense server, as shown in Figure 10, by adding new DNS entries, firewall rules or modifying the routing table. This traffic is then inspected using machine learning techniques and when certain criteria are matched (e.g. user authentication request), a certain 2FA mechanism is activated. The introduction of this proxy into the organization centralizes the MFA processes, eliminating in this way the need to integrate the MFA applications in the network, one by one, with the MFA method of choice selected. If the user is successfully authenticated, he or she will be allowed to access the resource.
This article was based on the section of the research paper titled Multi-Factor Authentication Implementation Guidelines and Best Practices written by Jose A. Rodriguez Albala. The complete work can be found here.