“In 2017 Google introduced a little security key to their all 89 thousand employees and completely neutralized phishing. Since then they’ve reported zero accounts takeover and account takeover is a major component of almost every security breach.”
With these words, Marcin Szary, CTO at Secfense welcomed the audience of DMEA (previously known as ConhIT, the biggest healthcare event in Europe, and one of the biggest in the world).
DMEA has a long tradition of being a place where the most innovative technology companies show their most recent products and solution to healthcare professionals. That was the reason why we decided to showcase our cybersecurity tool during the event in Berlin.
Secfense mission is to always enable the best possible protection for all the apps within an organization. With no restrictions when it comes to verticals. Secfense security layer can be easily introduced in finance, insurance, utilities, healthcare, e-commerce, transportation, etc. The bigger the company, the more burning the issue is.
We help companies save time and money while improving their overall security strategy related to user authentication.
While DMEA, being a huge healthcare event, is dominated by big eHealth technology brands with some impressive stands and equipment DMEA organizers also made sure that the event will not miss an opportunity to show what new technologies and new start-ups can deliver.
A specially designated space during the show called Start-up CAFE was a special place where people responsible for new technologies from hospitals and clinics could come and see new ideas from new and interesting brands.
That was also the place where Marcin Szary had the pleasure to deliver his short speech and showcase our new demo and our new feature – microauthorizations and explain how User Access Security Broker can help eradicate phishing attacks in healthcare.
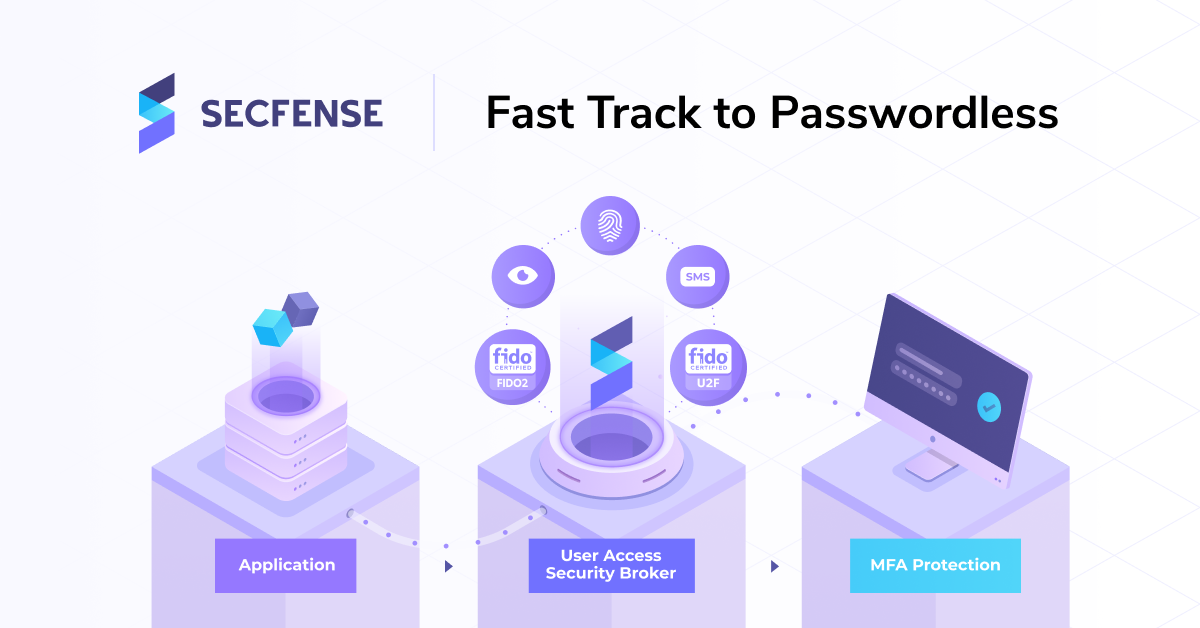
With Secfense we can help you mitigate the risks with the most impact on your users security without stretching your budget. We do so by introducing an intermediary layer that is spanned across the entire infrastructure and protecting users on the fly.
So we do not modify the applications themselves, but rather we put ourselves in a position where you can observe, analyze and modify traffic to them. So there is no costly software development involved, no third-party code in the application and no vendor lock-in, which is very important.
During the showcase, Marcin showed a live demo of Secfense deployment on a medical application. The whole presentation took less than 5 minutes which is twice as much as it’s necessary to deploy an independent security layer on a medical app without touching its code. We recorded the whole showcase, so you can watch it on our Youtube channel and see what the live product looks like.
An interesting thing that we showed for the first time was a feature that enables hospitals and healthcare institutions to protect some specific areas within the application (so the application is already protected by a password or two-factor authentication, but still, some areas require some extra authorization).
So with Secfense you can create another protective layer on top of this resource, so we can force users to re-authenticate every time they try to access it. We call it microauthorization. When the user tries to access a resource protected with microauthorizations, he or she will be requested to tap the security key again to re-authenticate. So there’s a 100% certainty that it’s still the same person behind the keyboard and not a malware controlled machine that stole the session. Secfense offers the easiers way to prevent healthcare phishing attacks.
Microauthorizations work in two scenarios:
- In the owner scenario, Secfense simply asks the user to re-authenticate.
- In the supervisor scenario, Secfense asks the privileged user (supervisor) for authorization
The only thing that needs to be done is for the admin to change the policy from owner to supervisor and that’s it. Next time the user tries to access a resource his or her security key will not be sufficient. It will be necessary to bring over the supervisor with the security key to grant access to this resource.
This seemingly small thing was a pain in the neck of lots of organizations, not only from healthcare but many other areas. Since big companies in most cases depend on the software from big vendors it’s often hard or even impossible to make some changes in the application code that will allow the application admin to add some features or extra authentication mechanisms.
With Secfense this is no longer a problem since all these things can easily be done without making even the slightest change in the application code.

So this all takes place in the middle of the space between the users and the applications so there’s no software development involved. You can build this protective layer on any app in minutes so if like Google you’d like to eradicate phishing in healthcare or other account takeover techniques, schedule your free consultation where we will explore with you all the available options you have to protect your organization against phishing, credential theft and inside frauds.
And here’s a couple of useful links where you can dig more on the subject of cybersecurity challenges in healthcare and how to deal with them: