2FA for enterprises
Two-factor authentication (2FA) is a well-known access control mechanism. Despite the wide range of benefits, the majority of big and medium businesses still haven’t decided to take a big step and introduce it across the whole organization. This situation is slowly changing, mainly due to the increasing level of cyber threats targeted at the user, but not only because of that. The 2FA is favored by the decisions of global authorities – such as the FIDO Alliance creator of the FIDO2 web authentication standard – and market demands.
With the advent of the Industry 4.0 era, new types of connections have emerged between information systems, in particular the one called Industrial Control Systems (ICS).
The necessity to integrate different areas entails the need to implement measures that provide greater control over access to connected systems. The use of 2FA allows organizations to add another layer on top of the authentication process.
- How does this translate into organizational security?
- Which two-factor authentication method is the best?
- Is 2FA a way to secure remote connections?
And what benefits will organizations bring about using these funds?

Popular two-factor authentication methods
The traditional login process is determined by applying the correct user credentials, then the identification takes place. The application is informed who is trying to access it (user login) and then who authenticates (enter the password). If “something you have” is added to this equation (eg U2F security key) or “something you are” (eg fingerprint, i.e. biometric authentication), we get two-factor authentication. The method is based on the assumption that an unauthorized user will not simultaneously have all the elements necessary to gain access.
A special case of 2FA is authentication step-based. It is based on two phases, ie authentication through the credentials and then eg by sending a one-time password via SMS (known as OTP – One Time Password). This of course provides an increased level of security because we have to show that in addition to knowing the login and password, we are in possession of the telephone to which the code was sent. Unfortunately, this involves a risk: these passwords OTP can be remotely intercepted by hackers.
A similar problem occurs with applications that generate codes (eg Google Authenticator), where the principle of operation is identical. The user, during the logging process, receives a code generated by the application and then enters this code during the second step of the login process to confirm its identity. Although the code is generated directly in the authenticating application, it requires access to the Internet. And this – in an extreme case – can end in the takeover of control over the whole device.
This type of second-factor authentication is far safer than using password-only protection, but it still leaves space for potential cybercriminals. It is worth having that in mind when deciding what type of authentication mechanisms and security policies should be applied in the organization.
A far better alternative to OTP (one-time passwords) is so-called biometric authentication. Voice recognition, eye scanning, fingerprint reading, all are much more serious challenges for the hacker. Therefore, these are usually the methods applied on a large scale in places with increased security requirements. Unfortunately, although the “falsification” of human physical attributes is extremely difficult in practice, it is not impossible.

Considering all pros and cons of 2FA methods it seems that the most effective authentication mechanism at this point are the physical tokens, so-called U2F (Universal 2nd Factor) keys, where passwords are directly on the device. This method has been applied by Google and none of their employees has been successfully compromised ever since.
Demand for 2FA in industrial environments
In IT environments, there are a number of activities such as software updates, maintenance, or configuration changes that are performed periodically and are necessary for the proper functioning of systems. Sometimes it is possible to remotely perform certain tasks by employees who are outside the company or people outside the organization. The phenomenon of outsourcing has become a reality in many industries, also in the case of remote access to the organization’s resources. In industrial sectors, we usually deal with a multitude of software from different vendors and technology providers. What’s more, these are often environments where access to critical infrastructure translates into people’s lives and health. It is crucial to provide appropriate security mechanisms when providing remote access to resources.
All remote access to industrial control systems must be adequately protected, controlled, monitored and recorded. Therefore, it is important to have visibility on devices that request access and their rights. If the infrastructure allows it, the devices are verified using the 802.1x protocol along with a centralized authentication service (eg Active Directory). What’s more, for a VPN it would be good to add an encrypted layer using SSL.
However, to increase the level of security in external access, it is recommended to add a second factor of authentication. It could be implemented in SCADA applications, operator stations, virtual desktops and other elements considered critical for OT infrastructure. Also, access to some industrial network devices, eg PLC controllers, is via virtualization of the connection. Most production environments limit the security mechanism to connect using a VPN client. Meanwhile, from the moment the connection with the production network is established, the actual access to the controller has a space in which an additional mechanism can be placed.

How does two-factor authentication improve security?
Implementation of a strong two-factor authentication method will allow mitigating the most frequent attacks. Especially attempts to steal access credentials for critical services. Some of the vectors used by cybercriminals in such attempts include:
- phishing campaigns
- exploiting 0-day and other vulnerabilities
- malware infection
- brute force
- and dictionary attacks on various systems.
In such cases, if the potential attack is successfully started, the multi-factor authentication mechanism will stop the threat. Since you will need to provide a second factor of authentication, the attacker won’t be able to obtain control over systems. Even if the credentials will get stolen or compromised the criminal will not be able to break in.
Remote access control in combination with 2FA is one of the best security practices in organizations, especially those with an increased risk of being attacked. And the industrial sector with a large critical infrastructure definitely falls into the increased risk group. Like it was mentioned at the beginning of this article, despite the huge role of multi-factor authentication mechanisms in the scale of the entire organization’s security, many companies still haven’t decided to implement it.
The reasons were:
- the complexity
- time-consuming nature and
- wide scale of difficulty related to the implementation of the additional authentication layer
This is particularly important in environments where the infrastructure is heterogeneous and many places require an individual approach. Fortunately, there are solutions on the market that offer flexibility and adaptation to very high requirements.
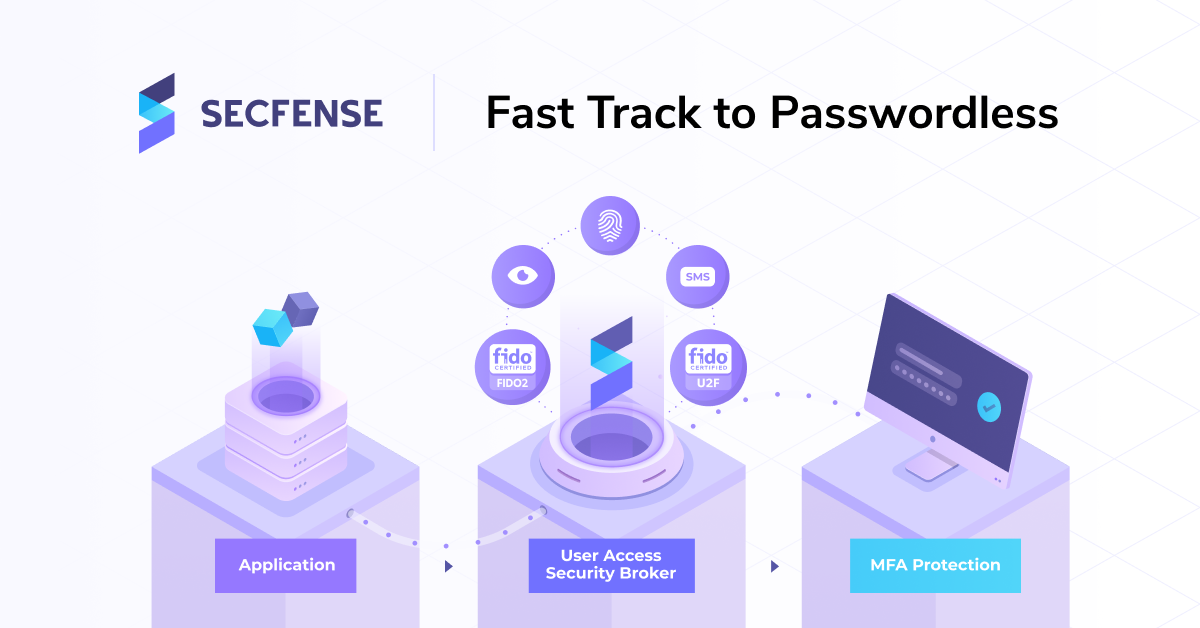
User Access Security Broker – a different approach to 2FA deployment
User Access Security Broker mechanism is based on the following factors:
- traffic inspection and learning – traffic flows through a proxy
- pattern recognition – if certain criteria are met, traffic is redirected
- activation of security modules – launch of the selected 2FA method
User Access Security Broker approach redefines the adoption of multi-factor authentication at scale. The solution allows big organizations to use any available 2FA method, such as U2F security key, biometric data (also using local authenticators with Webauthn), or mobile application authenticators. The broker is implemented between users and applications to which they have access.
- First, the broker learns the traffic patterns associated with authentication.
- Then enforces 2FA login or other defined actions.
This is done without disrupting the existing application code or interfering with application resources such as databases. The implementation takes place in any web application in a matter of minutes or hours. There is no third-party code residing in the physical programs and applications of the organization, and hence – no threats and vendor lock-ins from the supplier.
Taking one step further in User Access Security Broker mechanisms you will get a thing called microauthorizations. This idea is based on adding an extra authentication layer even deeper, in specific areas of the application. There are places that have many resources that require additional protection. Thanks to microauthorizations, each time a user attempts to access a specific resource, he will be asked for additional authentication.
What are the benefits of investing in a user access security broker instead of simple 2FA deployment?
User Access Security Broker offers a simplified integration of security mechanisms in all business applications without interfering with the source code. This means:
- flexibility – the ability to choose the authentication method that best suits the organization,
- independence – client application maintenance and changes in a code do not affect the functioning of a user access security broker,
- unified rules – security broker allows to apply exactly same access policies and same rulers across all the applications within the organization,
- security of the entire organization – user access security broker covers the entire infrastructure (local + cloud)
Trend Micro in the last report exchanged human-machine interfaces (HMI) as the main target of cyberattacks in the industrial sector. These attacks account for over 60% of hardware exploits. HMI interfaces are one of the most important elements of 4.0 industry technology, so it is becoming safe to do so. Strong authentication in this case may be the most efficient solution to the problem. – Antoni Sikora, Head of Growth @ Secfense
The future with 2FA
It’s highly probable that more and more organizations will introduce 2FA authentication policies across all their resources. These include SCADA systems, remote desktop services, connection virtualization, etc. Where it is not possible to implement 2FA mechanisms, it is recommended to restrict access and increase activity monitoring. At the smaller scale, or for individual purposes, it’s also wise to consider using the password managers with 2FA such as LastPass or OnePassword.