Security of web applications
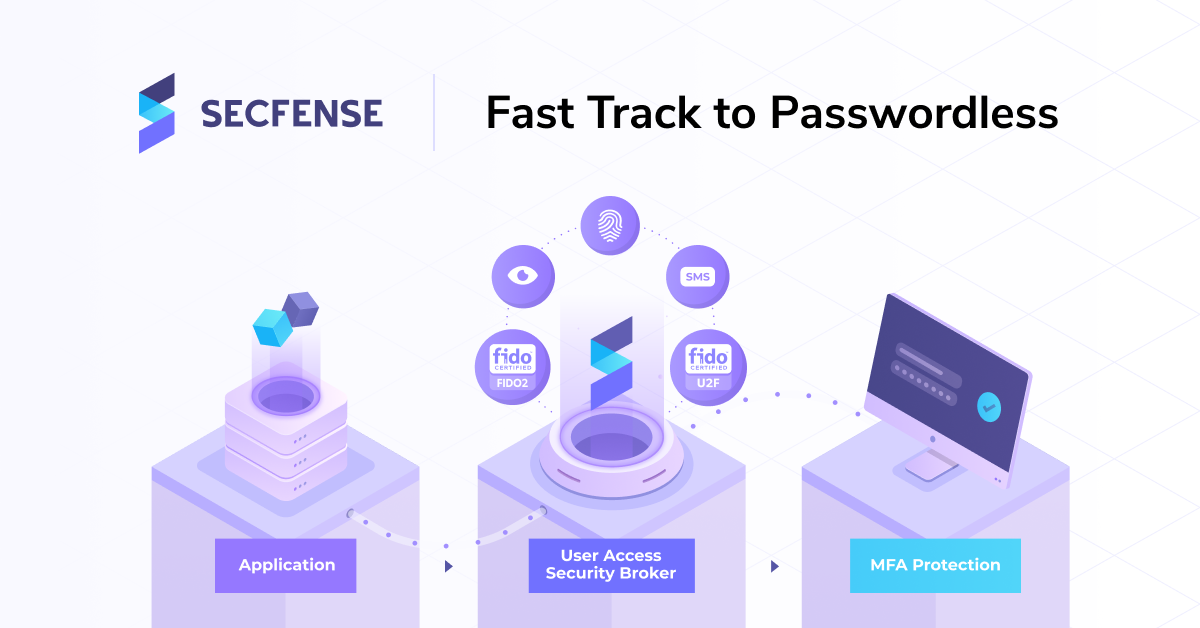
IT architecture in large organizations usually means a heterogeneous environment developed over the years with the use of many different technologies. At the turn of the last decade, the migration of organizations from fat client applications to web applications began. This change has opened the way to better securing these systems with multi-factor authentication (MFA). This change was also the impulse that led to the creation of Secfense company and development of the User Access Security Broker.
Desktop applications, web applications and data security
Marcin Szary, one of the company’s co-founders and creator of the User Access Security Broker, talks about the beginnings of Secfense. – Despite the web trend, the vast majority of applications after migration to the web still remain secured with only one weak component in the form of a password. It was the beginning of 2018 when together with Tomek, my current partner and then a long-time collaborator, we started to wonder why the approach to web application security is so old-fashioned? After all, the web opens up huge possibilities. Is there something we could do to change the status quo? These questions were the starting point for the idea that Secfense was born from.
Modern applications and the old approach to security
Technology vendors that used to provide client-server software have recently been increasingly offering a “web” model in which the browser is the client. Despite this enormous change, the mindset of companies looking to keep their data secure does not change. As if the transformation to the web did not take place at all. The approach of many organizations to cybersecurity is still very traditional. However, the web model opens up enormous possibilities allowing for more effective, easier to use, and scalable security improvement in the organization.
The old application security paradigm
The approach of companies wanting to protect their software is usually as follows. Application A, which is a closed black box (closed server, closed client, closed protocol) should be secured with strong authentication. The traditional approach, in this case, is to introduce strong authentication on the server, i.e. the place where the application is located, while modifying the client software so that it “understands” this change.
HTTP protocol changed the rules of the game
This traditional approach, however, omits a very important element that did not exist in the client-server model but exists in the web model. This element is the HTTP protocol. The HTTP protocol is an open and standardized place where you can “plug in” and influence the interaction between the application and the user without changing any of the parties.

A new approach to the security of web applications
At Secfense, we try to change the way organizations think about protecting user identity in applications, says Marcin Szary. The Secfense broker that we have built proves that strong authentication can be added in transit (HTTP protocol), and not necessarily by interfering with the application itself (whether on the server or client-side).
Secfense and strong authentication in web applications
In 2018, the idea of the Secfense broker seemed very futuristic and uncertain. The idea arose before the FIDO authentication open standard came into force and completely changed the rules of the game. – says Marcin. We felt that the entry of this standard was inevitable and its adoption could become our tremendous opportunity. Obviously, we were not 100% sure if and when it would happen, and above all how the tech giants would react to it.
FIDO Standard
The FIDO standard was approved by the World Wide Web Consortium (W3C) in March 2019 and changed everything. Microsoft, Facebook, Google, and Amazon decided to adopt it in their solutions, and this entailed most of the technological world, a few months later Apple joined (or basically returned) to the standard, which was the final seal that FIDO will stay with us for good.
Why is FIDO so important in the history of Secfense?
When the co-founders of Secfense started working on the MVP (minimum viable product, i.e. solution prototype), which later turned into a User Access Security Broker, there were already tools on the market for strong authentication with the most powerful of them – the U2F (Universal 2nd Factor) cryptographic key. The subject of which extensive information can be found here.
However, the possibility of using the benefits of U2F keys was very limited in 2018. In order to secure applications with U2F keys, the organization had to force its employees to use a specific browser, install a dedicated FIDO extension, and additionally integrate this emerging standard with the applications themselves. However, we were counting on the fact that the adoption of the FIDO standard is around the corner … – says Marcin
Building awareness about FIDO Authentication
The FIDO open standard was one of the most important transformations in the cybersecurity world in recent years. Despite this, most of the people we spoke to in 2018 did not hear about FIDO. Multi-factor authentication already existed in consciousness, but the opening up and standardization of a much stronger authentication method was completely new to many.
U2F Keys
U2F keys offer the strongest method of strong authentication today. However, in terms of cost and utility, they may be inaccessible to many organizations. Why? Because each key is a cost (currently around $ 20-50), which with thousands of employees is a huge expense. They can also be damaged or lost, which causes additional costs and inconvenience.
The FIDO standard, which made it possible to replace the U2F key with local authenticators (for example a smartphone or a laptop with a biometric reader) eliminated these restrictions. In this way, the user can decide whether he prefers to authenticate using a device that supports this standard, and the user has it anyway (such as a smartphone), or whether he or she prefers to authenticate with the U2F key.
The U2F and FIDO2 keys are not the same as security tokens
A common misconception is confusing old security tokens with U2F or FIDO2 keys.
If we ask a person who has been working in the corporation for several decades what a security token is, he or she will probably indicate a token in the form of a key ring that generates one-time codes (i.e. PKI tokens).
It cannot be denied that this device has some features in common with U2F or FIDO2 keys. The keys are usually inserted into the USB port. Both keys and PKI tokens also use asymmetric cryptography. However, the similarities end there.
In the case of U2F or FIDO2 keys, the device works immediately after taking it out of the box and connecting it to the computer. You can buy such a key online, unpack it and secure your social media, e-mail box, or in fact any other application, protected by the Secfense broker.
Old PKI tokens were associated with a huge bureaucracy in the work of the cybersecurity department. The procedure for initializing these tokens was very complicated. Uploading and managing certificates on the server-side, installing middleware on computers so that the key can work …
PKI tokens mean many sleepless nights and numerous gray hairs on the head of many CISOs. The U2F and FIDO2 keys are a ‘game changer’. A device that changes the rules of the game and turns the old bureaucracy and the related problems of PKI tokens upside down.
Why is the FIDO standard so safe?
The FIDO standard keys and local authenticators supporting the FIDO standard allow user authentication only on the domain with which they are associated. Once a cryptographic key is registered in a given domain, it will not allow authentication in any other domain that will impersonate that domain. This solves the problem of social engineering and phishing, i.e. a situation in which the user gets cheated and does not notice that the domain he or she wants to log in to is false.
Secfense, strong authentication and passwordless
The idea, born in 2018 in the minds of Marcin Szary and Tomasz Kowalski, in 2021, has already been appreciated by companies such as BNP Paribas Polska bank or PKP Intercity. The Secfense broker already allows thousands of users to implement strong authentication on any number of applications. What are Secfense’s plans for the future?
Secfense – the shortest path to the future without passwords
The future is passwordless, i.e. authentication without a password, says Marcin Szary. Passwordless is the holy grail of cybersecurity, and for Secfense, the next step in User Access Security Broker development. An organization that has decided to use Secfense broker will be able to decide if and when to migrate its users and applications to be completely passwordless, that is to completely eliminate passwords and replace them with strong multi-factor authentication.
In the next article, we will tell you what the Secfense approach to passwordless is and how we want to enable organizations to completely eliminate passwords. We invite you to read our newsletter, visit our blog and get in touch!