One view suggests that enhancing an internal network’s security can be achieved via stringent user access management, such as privileged identity access management. This involves stringent rules on host access, port access, and the kind of data being transferred. If a user’s account gets compromised, these measures help reduce the fallout of a cyber attack. However, I contend that these restrictions don’t replace the need for strong authentication. Rather, they pair seamlessly with it. Here are some reasons why:
Identity and Access Management System plus Strong Authentication
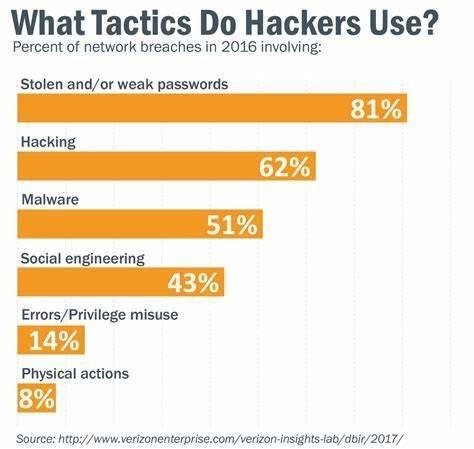
- Reports indicate that password hijacking, achieved either through cracking or theft, is a common method of infiltrating computer systems. This suggests that safeguarding passwords is a significant step in warding off a majority of cybersecurity threats. However, we can’t overlook other vulnerabilities.
2. If a breach does occur, restrictions from the identity and access management system only come into play after the fact, while authentication is designed to prevent it. Hence, I’d consider multi-factor authentication (MFA) as the first line of defense, followed by access restrictions. If resources compel me to focus on one aspect at a time (due to budget, technical, or organizational constraints), I’d start with MFA.
3. We must also consider the effort-to-outcome ratio. In point number 1, we highlighted that tackling weak and stolen passwords can prevent over 80% of system breaches. The complexity of fortifying internal network security can vary across organizations, and utilizing a unified environment or identity access management tools to oversee a diverse network can expedite the process.
Firstly, it requires understanding resource utilization and discussing potential changes with all business departments or individual users. There’s no assurance that any agreement reached will remain effective indefinitely. Implementing MFA also demands substantial effort, particularly in traditional approaches where every application needs modification to require a secondary authentication component (known as 2FA – two-factor authentication). This could involve providing a one-time code, using a U2F/FIDO2 key (dongle), or scanning a fingerprint.
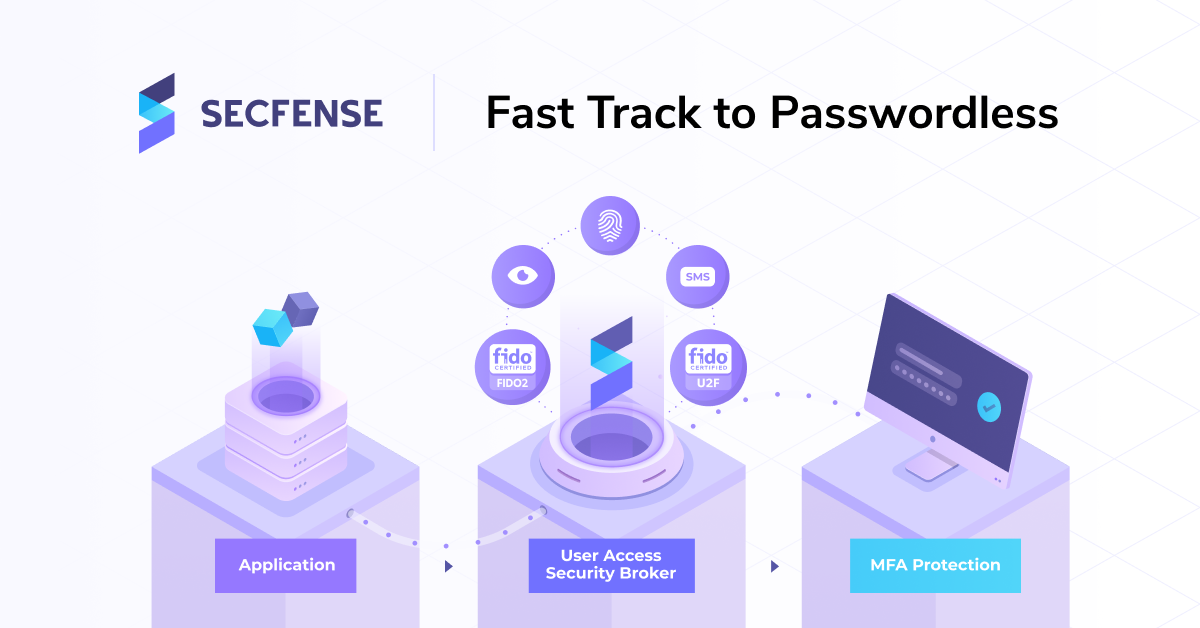
And what if there are numerous applications? And some of them can’t be reworked easily (due to being third-party or built on outdated technology)? Thankfully, Secfense offers a solution called User Access Security Broker that enables strong authentication without needing to modify applications. It functions as a bridge between the user and the application. For the user, Secfense introduces 2FA, and after authenticating, they can connect to their application. From the application’s perspective, it only grants access to users who have authenticated securely.
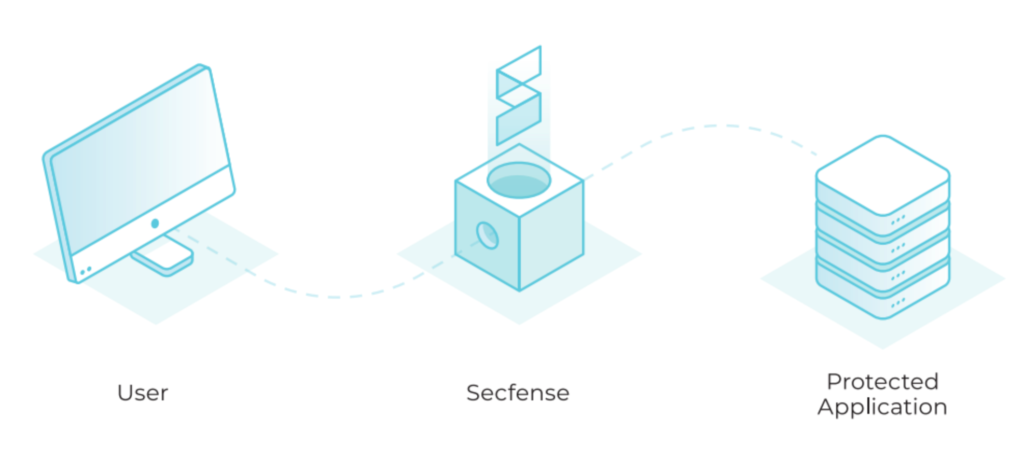
Implementing strong authentication with Secfense not only guards against a major threat source but is also quick and straightforward.
In conclusion, I advocate for strengthening internal network security through various restrictions and implementing strong authentication. You can start by learning more about multi-factor authentication (MFA), and two-factor authentication (2FA) and exploring the User Access Security Broker.
If your organization already has strong authentication mechanisms and the workforce is well-versed in cybersecurity best practices and password-related risks, perhaps it’s time to delve further into zero-trust security and take a step toward passwordless authentication with Secfense. User Access Security Broker can be a key component in this transformation. Book a call with us, and during a 15-minute demo, we will show you how to add MFA to any of your apps in minutes and how to transform your company into a passwordless organization within days.