So-called ‘secure networks’ no longer work
The world of cybersecurity keeps chasing newer, better, and more effective ways to protect against data leaks. The traditional model that used to focus IT security efforts on the edge of the network (the philosophy of building the so-called “castle and moat”) does not work anymore. Expenses on prevention keep increasing but at the same time, the costs of cyber ransoms and costs of fixing the damage made by attackers keep increasing as well. There’s one model though that is becoming more and more popular among cybersecurity experts. This model is called Zero Trust. But what is it and how to introduce zero trust in an organization?
Zero Trust Network Model was first mentioned in 2010 by John Kindervag. Since then many CIOs and CISOs have introduced the Zero Trust model principles to protect their organizations globally.
What’s so special in the Zero Trust Security Approach?
The core of Zero Trust is the assumption that organizations should never automatically trust anything or anyone inside or outside the network. Instead, they must always verify any attempts to connect to the systems before granting access to them. The strategy around Zero Trust comes down to basically not trusting anyone. This means cutting off all access to IP addresses, machines, systems, resources, etc., until the network knows who the user (or system) is and whether it has the appropriate permissions or not. In other words, the Zero Trust model completely discredits the “castle and moat” philosophy, in which the organization is focused on defending the perimeter, and assumes that everything inside is safe and not subject to access control.
IT security experts relentlessly repeat that the “castle and moat” approach does not work. They point out to the fact that most data leaks occur when a bad actor is already within the corporate network after successfully breaching a firewall. When the intruder is in he is able to navigate through internal systems without any problems.
There are more reasons why Zero Trust has been gaining so much popularity. Currently, in most cases, the “castle” itself does not function in isolation from the rest of the IT world. Corporate data centers do not only support closed networks, but also maintain applications in the public cloud, accessible anytime and anywhere, also from the public internet.

What does the Zero Trust consist of?
The Zero Trust approach builds on a variety of existing technologies and management processes to secure the organization’s IT environment. The model uses information about users, their locations, and other related data to determine whether a user, machine, or application requesting access to a particular system or resource can be trusted.
It uses methods and solutions such as:
- multi-factor authentication,
- IAM,
- Visibility,
- Automation and Orchestration,
- Security Analytics,
- Emails and Files Encryption,
- Scoring and File System Permissions.
Zero Trust also requires that you define access management rules, such as providing users with the lowest level of privileges necessary to complete the desired task.
Network security is therefore designed from the inside (from the user level) and not from the outside (“from the castle and moat”).
Zero Trust is not more than a security policy. It is a continuous process and way of thinking about security. It requires constant efforts to monitor, audit, and improve.
Human Factor – the critical aspect of cybersecurity
It should not be forgotten that in the foundations of information security, the most important place is always the human being, supported by technology and processes. Lack of cybersecurity training and lack of a continuous awareness of employees about the dangers of the digital world may wipe out all efforts and waste all invested resources. The transition to the Zero Trust model should therefore be an integral part of any organization’s digital transformation strategy.
From Zero Trust Model to Passwordless Authentication
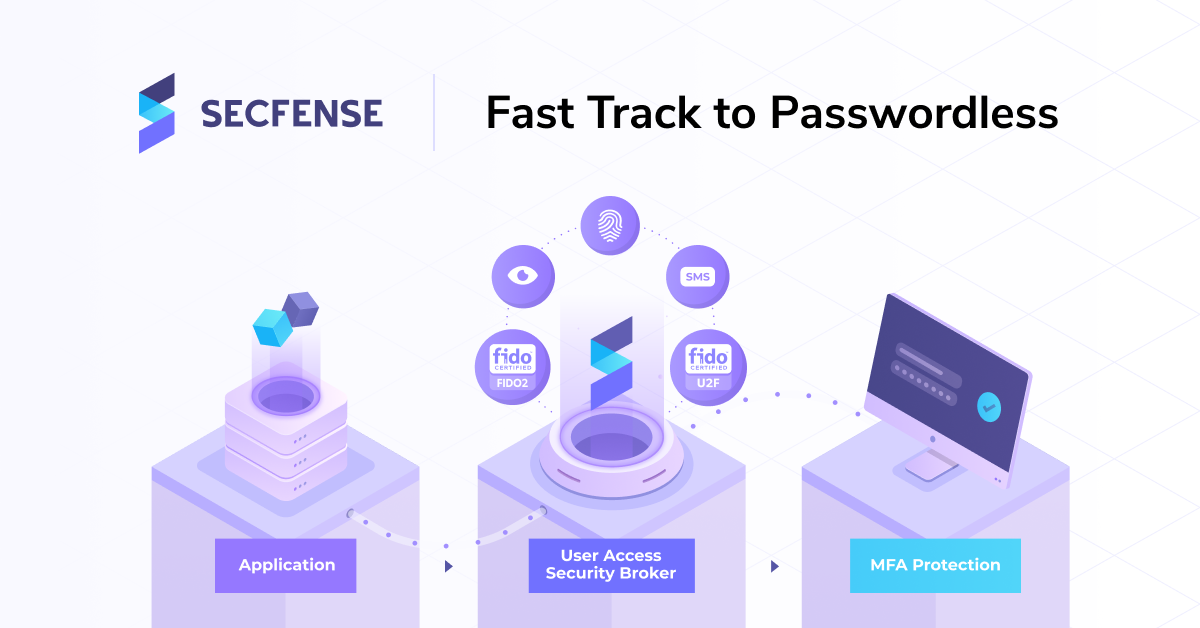
Passwordless, the holy grail of cybersecurity. There are many roads that lead to zero trust security and passwordless authentication. One of the approaches that help companies enter the path to zero trust security is the User Access Security Broker. Secfense has designed the broker approach with one goal in mind. To offer the easiest and fastest transition from passwords, through strong authentication to fully passwordless authentication within the entire organization.
The video below shows our short showcase that we did during the Zero Trust Interactive Forum, a virtual event hosted by the CloserStill group.
The goal of the presentation was to show how to break legacy systems limitations and how to introduce zero trust globally. We also touched on the topic of passwordless authentication and explained our approach to scaling it without touching the code of the protected application.
- Is it possible to protect legacy systems in the same way as cloud apps?
- Can you integrate new security solutions without any software development?
Watch the video to get the answers. During this showcase, you will also:
- See the live deployment of multi-factor authentication on a legacy system.
- See our approach to easy and fast passwordless authentication deployment.
Zero Trust & Passwordless Authentication FAQ
We dedicated a big part of our presentation to answering the most common questions that we receive from our customers. The video below will take you straight to the part where we answer the questions listed below:
- What distinguishes Secfense’s approach to strong authentication from other methods of implementing additional security?
- Does Secfense work in the SaaS model or can I run it on my network?
- What does the implementation of Secfense look like?
- If I already have second-factor authentication in place, should I still be interested in Secfense?
- How does Secfense store user passwords?
Scaling the Zero Trust Model Within the Entire Organization
Everything that was shown during this demo is something that you can easily try out in your test environment. If there’s one thing we would like you to remember from this showcase it would be the SCALABILITY OF ZERO TRUST.
Our goal is to scale zero trust within the entire organization.
So if you’re struggling with unifying your security policies and you fight with a bunch of legacy apps then we really encourage you to talk to us and see if we can help.