There has been a lot of buzz in the cybersecurity internet lately about MFA bombing or MFA fatigue, two names for the same method that cybercriminals use to bypass multi-factor authentication. In this article, we explain what MFA bombing or MFA fatigue is and how to defend against it.
MFA bombing, and Uber attack.
MFA bombing became famous after the recent attack on Uber. An Uber employee’s account was compromised as a result of sending hundreds of compromised push notifications. Deceived Uber employee has let a cybercriminal into the corporate network and thus caused an image crisis for the transportation technology giant.

How does MFA bombing work?
MFA bombing is nothing more than persistent harassment of the user with subsequent push notifications urging them to accept the transaction. The cybercriminal hopes that the user will get tired (hence the name MFA fatigue) of rejecting subsequent notifications and, at some point, will simply agree to the query appearing every now and then on the smartphone screen.
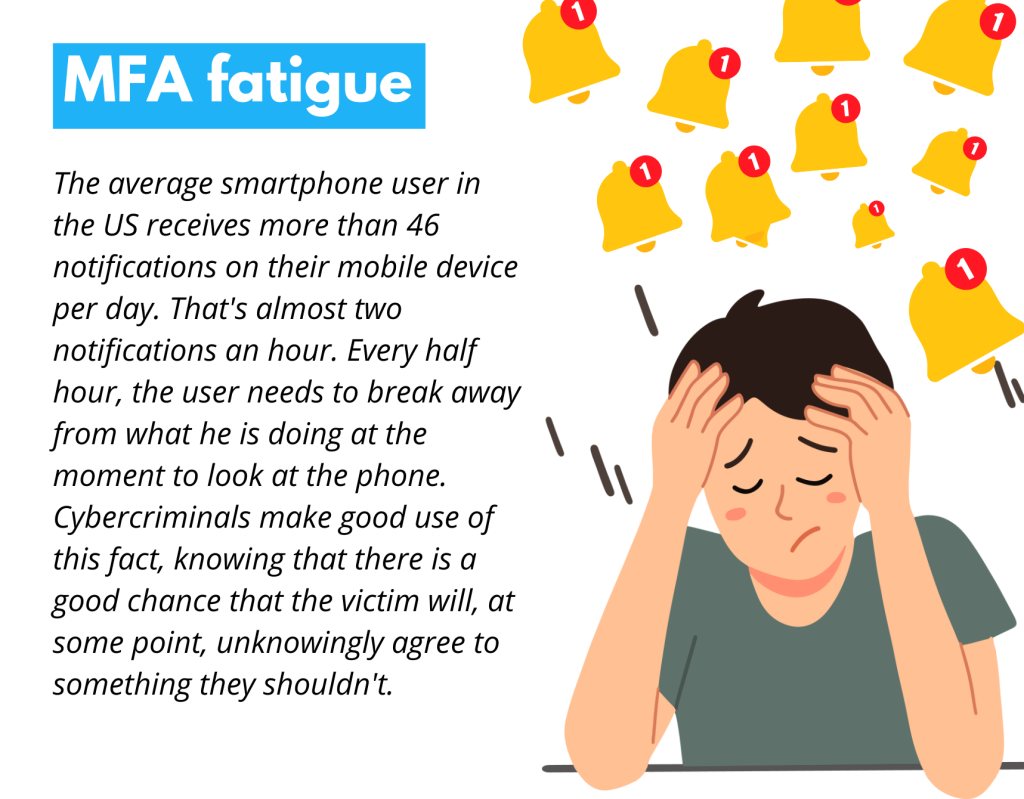
MFA fatigue
The average smartphone user in the US receives more than 46 notifications on their mobile device per day. That’s almost two notifications an hour. Every half hour, the user needs to break away from what he is doing at the moment to look at the phone. Cybercriminals make good use of this fact, knowing that there is a good chance that the victim will, at some point, unknowingly agree to something they shouldn’t.
How to defend against MFA bombing? How to avoid MFA fatigue?
CISA, the cybersecurity and infrastructure agency has consistently urged organizations to implement MFA for all users and all services. However, the organization emphasizes that not all forms of MFA are equally safe, as the example of MFA bombing, which efficiently circumvents MFA based on push notifications, is perfectly demonstrated.
As a result, the new CISA guidelines emphasize the need to use an MFA resistant to this type of attack, an MFA that does not use push notifications, i.e. authentication based on biometrics (fingerprint or face scan) or physical hardware keys.
Using this method as the second factor of authentication and eliminating the push authentication option fully protects against phishing and social engineering. The user has the option of logging in to the application only by confirming his identity biometrically or with a physical security key.
How to implement FIDO2 authentication?
The best way to start using FIDO2 authentication based on both biometrics and hardware keys is to use the user access security broker approach. This approach to the implementation of MFA in organizations developed by Secfense allows you to implement MFA on any application in a no-code way, i.e., without the need to interfere with its code. The ability to install MFA without coding allows the organization to implement scalability, i.e., the ability to use MFA on any application and any number of applications. This means that the Secfense broker gives you the opportunity to secure the entire company and all applications with authentication resistant to phishing, MFA bombing, or MFA fatigue, in other words, attacks on older MFA methods.
What if currently secure MFA methods are defeated?
Nothing is permanent in cybersecurity. Criminals are finding new ways to circumvent more and more advanced defense methods. The trend is also heading in a direction unfavorable for companies operating on the Internet. A few years ago, it was said that if cybercrime were a country, it would rank 13th in the gross domestic product compared to other countries. Statistics from 2021 indicate that in just a few years, cybercrime has gone up ten places in the ranking and is now in third place after the economies of the US and China.
Timeless security
It is, therefore, reasonable to suspect that the currently most secure MFA methods will one day be defeated. The Secfense broker has a chance to protect the organization against the time factor as well. The characteristic of this technology is that it allows you to implement any authentication method in the same easy way. Therefore, companies can reach for the currently most secure FIDO2 standard, as well as use methods previously used in the organization. The broker also guarantees that future yet unknown authentication methods will be added in the same easy and scalable way always to ensure the best level of security for user and application authentication.