Recent cyberattacks show that politicians become victims of cybercriminals more and more often. What methods do criminals use and what steps can be taken to prevent them from stealing private data?
Politicians under cyberattacks
Is it even possible to prevent the attacks and the leak of confidential information? Many organizations – companies and offices – are hacked more often than ever through credential theft. Politicians from all over the world are being affected, as well. Leaks of important and confidential data from email accounts or badly secured applications are more and more frequent. One of the recent scandals concerns Poland where cybercriminals managed to take over the email account of the Chief of the Chancellery and published the content of official correspondence. But this is not a single case. Other countries are being attacked as well, as in the case of the United Kingdom. What is the criminals’ way of acting? How should politicians and employees of crucial national institutions behave to protect against such cases?
Recent cyber attacks in the UK
As the numbers are growing, the problem of email accounts takeover becomes from crucial national and medical institutions has become a concern for almost every country. In the past 6 months, attackers took over classified information related to British aid projects financed by National Security Council intended to counter-terrorism and building stability overseas. In February 2021, a breach of sensitive data was reported at Oxford University laboratories researching Covid 19.
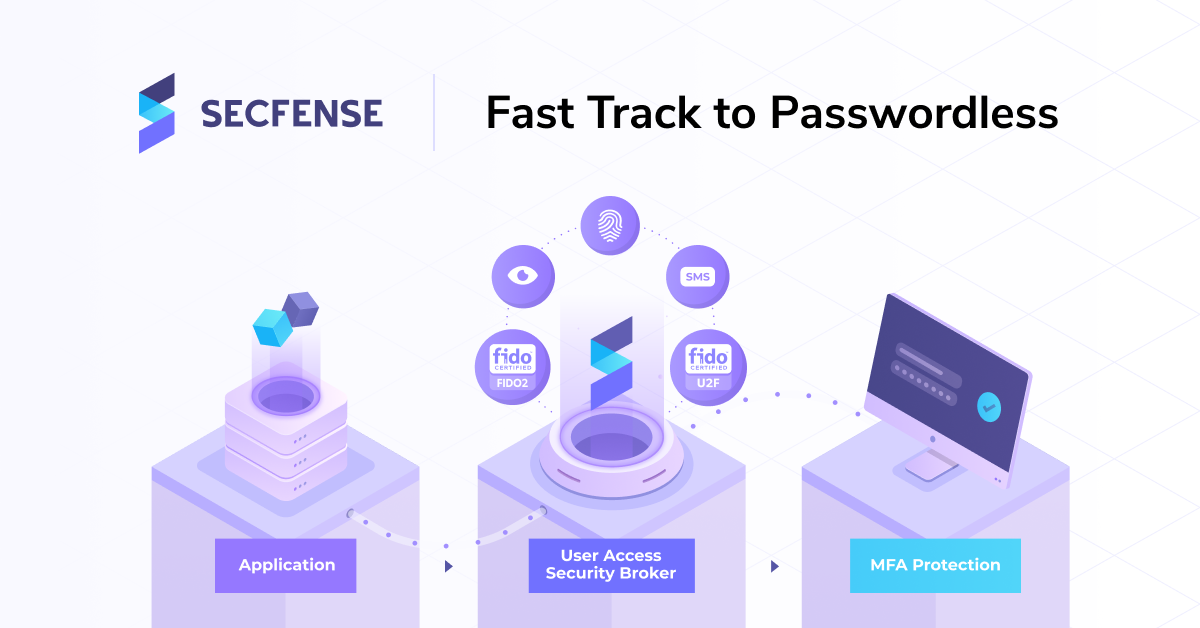
“Cyberattackers obtain user online credentials through phishing scams”, Tomasz Kowalski, Secfense CEO, said. Secfense built User Access Security Broker solving to solve the issue of difficult adoption of strong authentication and, thus, unlocked the potential behind the Universal 2nd Factor standard, i.e. U2F. “This is exactly why everybody, especially, individuals with access to sensitive information, should use strong authentication based on multi-factor authentication (MFA). U2F or FIDO2 based authentication can give you the biggest level of security possible. The most important part of online security is to make sure that the person behind the computer is actually the person who is authorized to do so. And not a cybercriminal using a stolen password”.
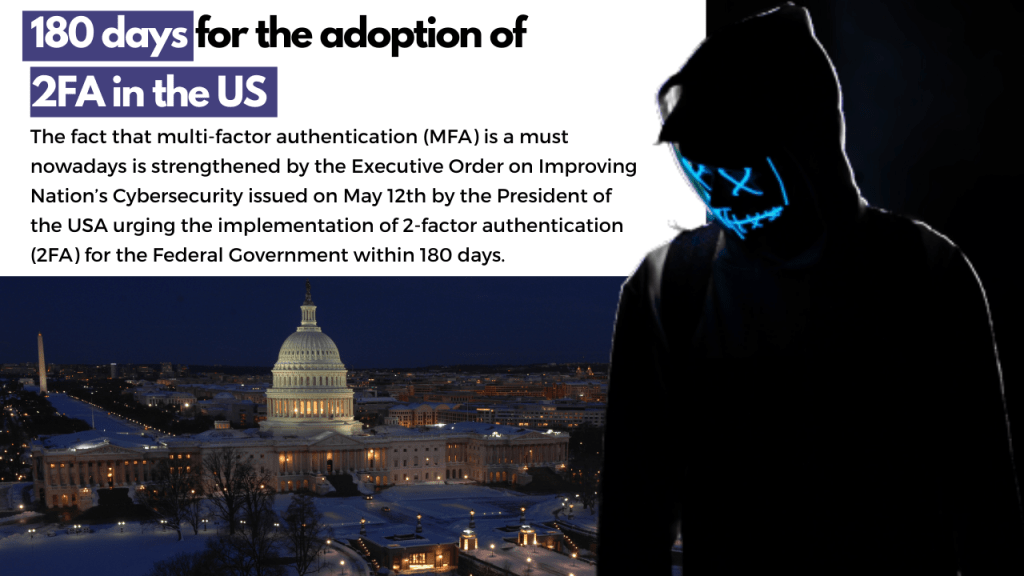
180 days for the adoption of 2FA in the US
The fact that multi-factor authentication (MFA) is a must nowadays is strengthened by the Executive Order on Improving Nation’s Cybersecurity issued on May 12th by the President of the USA urging the implementation of 2-factor authentication (2FA) for the Federal Government within 180 days. Solar Winds U.S. cyber-attack 2021 only made things more important and more urgent.
This type of security measure was lacking in the case of Michal Dworczyk, the Polish Chief of the Chancellery, which, on June 2021, resulted in his private email account takeover (which by the way was never under any circumstance supposed to be used for official correspondence). This hack caused quite a stir since strategic and strictly confidential information of state value was taken over by unauthorized people.
“According to the domain’s owner where the Polish politician’s account was hosted, the access to the account was obtained as a result of providing correct login and password”, Kowalski added. “It may be assumed that the cybercriminals either extorted the password from the Minister’s wife or took advantage of the fact that she used the same password in other services and obtained it from one of them”.
State matters kept on Gmail
The use of private email accounts for official business within state administration is not only a Polish flaw. According to Sky News, in 2020 alone, as many as 151 security breaches reported by the British Ministry of Defence were caused by the transfer of secret information from the government-secured network into private email accounts.
“Even the people who have access to the most confidential national information are hard to train and discipline. It is, therefore an imperative to speak loudly about comprehensive use of multi-factor authentication and about replacing passwords with better alternatives and therefore going passwordless.” Tomasz Kowalski further explains. “The second factor could be both physical keys or biometric scanners built into laptops or smartphones. It is crucial to secure all the apps used by employees and politicians. Luckily, there are a number of non-invasive ways to use any method of multi-factor authentication, including cryptographic keys, that does not require changes in application code and therefore can be easily introduced to any app“.
U2F Keys for the Polish Government
After Minister Dworczyk’s email leak scandal, talks about the purchase of physical cryptographic keys (U2F) for the Polish government have begun. However, whether the U2F keys will protect all the government applications and will politicians actually use them when they are ordered to do so remains in question.
Multi-Factor Authentication for Politicians
Either way, today, multi-factor authentication is considered the most effective protection against information theft, including obtaining sessions from logged-in users, phishing, and man-in-the-middle attacks. All of us and, especially, people holding state positions, should immediately stop using passwords as the only online authentication and security confirmation. It is the passwords, often weak and identical in numerous services, that are prone to easy theft, which may result in not only the owner’s stress but also in a political crisis.
How to protect against cyber attacks
What measures should government officials take to protect their data against cyberattacks?
- Start first with the use of different passwords in different services. Never duplicate passwords or use many variants of the same password on different apps only using additional numbers of symbols.
- The use of password managers with a strong password and strong authentication enabled is a good way to start.
- It’s highly recommended to implement two-factor authentication (2FA) whenever and wherever it is possible.
- Never send sensitive information through private email accounts.
- Allow automatic updates of operating system and key applications. This will help you avoid problems related to software bugs and security holes.
- Do not react when someone asks for immediate provision of data, whether the request comes from an application or through an email demanding immediate reaction, or from a fake bank representative calling with a request for the installation of a phone application. If it’s super urgent then always be aware!
- Use Signal communicator for important messages. Signal is currently the most secure messenger application. In contrast to Whatsapp, not only does it provide confidentiality but it also maintains privacy of all conversations as it does not collect any connection metadata, i.e. the messages are encrypted therefore the application does not know their content, it also does not know who the participants of a conversation are.
Get in touch
For more information about implementing strong authentication on any application and introducing passwordless authentication in your company talk to us using our chat or schedule a discovery call.