Introduction
Without a doubt, COVID-19 is changing the way we work. Remote working, initially adopted only by a few businesses, is now becoming a forced trend in many organizations. A trend pushed by governments to suppress the quick spread of the disease caused by severe acute respiratory syndrome coronavirus 2 (SARS-CoV-2). However, this change from the traditional office setting to working from home might have a significant and long-lasting impact on cybersecurity. Businesses simply need to implement new measures to address the challenges caused by sending employees to work from home.
This article is a quick summary of a Threatpost cybersecurity poll that sought to learn more about challenges and remote work security best practices from the IT and security professionals on the front lines of the remote work cyber security strategy.
Poll Analysis
The poll sought to gather information on how prepared organizations are, from a security standpoint, to send people home to work. According to the results, 51.22% of the participants revealed that they were fairly prepared, with a few pools of people reporting challenges. 31.01% of the study subjects stated that they were confident and ready to move to 100% remote working. Another 12.2% indicated that they were ready to move a minority of their workforce to online, but believed their organizations had more work to do to implement their remote work strategy. Slightly more than 5% of the organizations were not prepared at all.
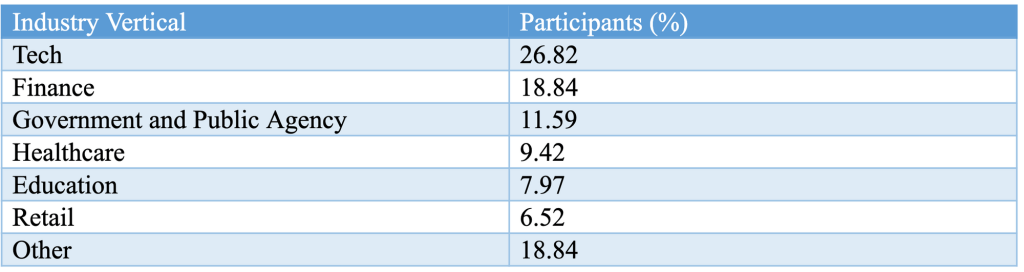
The study gathered responses and ideas from IT and security professionals in diverse industries as shown in the table below:
Different participants face varied challenges in securing their remote footprint. The poll revealed that user awareness security is the principal concern for businesses, as affirmed by 43.23% of the participants. 20.95% of businesses claimed that sensitive data now housed off-premise and transmitted via the open internet was a prime issue. Patching and updating and lack of footprint visibility continue to be a concern for 9.61% of organizations respectively. Other constraints mentioned by participants include mobile security (6.55%) and the cost of VPNs (5.68%).
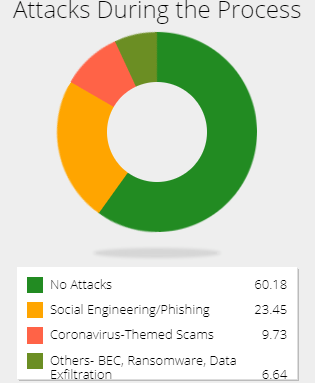
In the last couple of days, numerous security firms have announced the rise in cybercrime during the coronavirus pandemic, as attackers take advantage of the increasing amount of time people spend online while working remotely. To this effect, the poll sought information about organizations that have been attacked during this process. The study found that most of the firms have not been attacked, or they have not identified malicious activities. However, about 23.45% reported facing attacks via phishing and other social engineering efforts.
Organizations sending employees and students to work remotely have varying considerations about their weakest security links. Slightly more than half of the firms reported a lack of end-user security awareness as their prime consideration. The poll further discovered that other organizations were concerned about home Wi-Fi and network security (26.01%); personal devices and BYOD (17.49%); and cloud and SaaS applications (4.04%).
Expectedly, many organizations have not telecommuted before the pandemic. The study results revealed that 30.73% of the companies had less than 20% of their user base telecommuting before the pandemic. 26.83% allowed a handful and only as needed work from home, without full-time employees working remotely. Only 11.71% of the organizations allowed half of their employees to telecommute.
However, as the coronavirus pandemic continues to sweep the globe, and as nations and organizations respond through social-distancing measures, the numbers for telecommuting employees will change sharply. 81.68% of firms will allow more than half of their employees to work from home, while a few organizations, less than 20%, will keep working with a handful and only as needed workers remotely.
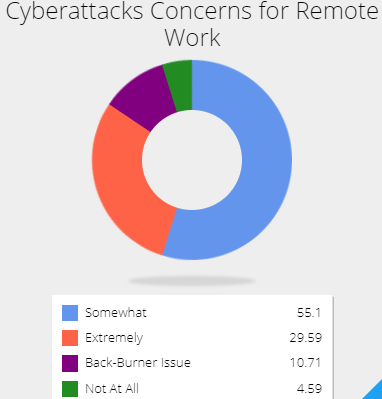
In the teeth of the pandemic, organizations are wary of the measures adopted abruptly. Among other things, they are concerned about cyberattacks targeting employees and students working from home, based on the fact that companies largely lack proper cybersecurity measures for the remote work strategy. The figure below shows the levels of concern about malicious activities targeting telecommuting strategies companies adopt.
In response, some organizations are putting in place measures to mitigate cyberattacks during the coronavirus pandemic, as discovered in the study. For instance, 34.34% of IT and security professionals are educating their end users on cybersecurity, while an almost similar number (33.13%) are implementing measures that ensure device security. Additionally, 19.88% implement a zero-trust approach and another 9.04% take inventory of devices connecting to the corporate network as some of the best practices for securing remote footprints.
Regarding end-device security efforts that IT and security professionals take, 30.86% of the participants revealed they combine a set of measures, such as multi-factor authentication for all applications (SaaS, mobile, cloud), secure devices, mandatory antivirus, hardware tokens, and obligatory strong passwords. 19.75% combine some of the measures, while merely 2.47% are still lacking cybersecurity best practices.
Organizations have largely used VPNs to prevent unauthorized access to business networks holding sensitive data. IT and security professionals use a VPN service to establish secure connections with remote employees. In this regard, companies equip their workforce with VPN access to resources as the poll results divulge. 37.74% of businesses make it mandatory for remote workers to use VPNs, while only 10.69% allows less than half of the employees to use the services. About 3.14% have in place alternative VPNs for their teams.
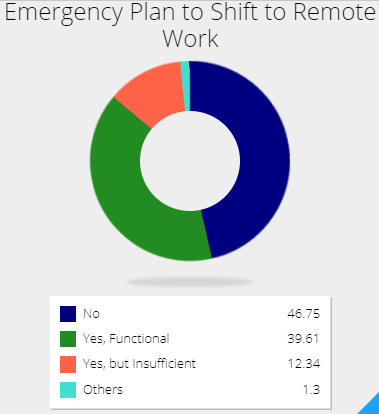
The study discovered that many of the security teams lacked emergency plans to shift an on-premise workforce to a remote one, as shown by the figures below.
Some IT and security professionals indicated they had specific concerns arising from working in a regulated industry. 23.91% were concerned about financial information while 17.39% were worried about securing healthcare data in a remote footprint. Only 4.35% were concerned about customers’ credit-card data. Similarly, cloud security has become more of a focus as the user base goes remote, with 44.54% of IT and security professionals indicating that they are more concerned about cloud service security.
Since undertaking a work-from-home strategy, only 18.58% claimed to have learned new security lessons. However, a huge number of the participants, 70.8%, alleged that cybersecurity challenges and the practices applied during the coronavirus pandemic were not new to them.
Final Thoughts and Recommendations
As coronavirus cases continue to emerge in every state and state, more businesses will continuously adapt to the swift action of teleworking to curb the spread of the virus. Unfortunately, this strategy presents cybersecurity challenges that organizations have optimally dealt with on-premise setups. In this case, IT and security professionals should devise and implement appropriate measures to secure their businesses while enabling the work-from-home approach for employees and students. It is a well-known fact that legacy cybersecurity measures, such as passwords, have outlived their effectiveness. Hackers steal or crack weak and default passwords, causing more than 80% of all data breaches, according to a research report by Verizon.
Ultimately, companies should investigate ways to adopt strong authentication mechanisms like FIDO2 web authentication standards or cryptographic keys. These measures offer a unique and secure way to access business networks and applications, where biometrics and other access credentials stay on the user’s device and are not transferred via the Internet to company servers. In effect, organizations can eliminate remote work security risks like social engineering, phishing, and all forms of replay attacks that compromise the safety of systems and sensitive data.
In the first week of coronavirus outbreak in Poland one of our customer reached out to us asking for a quick help. The goal was to protect two applications used by remote workers – Outlook Web Access and webVPN with strong two-factor authentication. In the result two days later more than 3,000 employees were able to add second factor to their user accounts. Depending on client remote work security policy some of them were asked to use application based authenticator, and some (depending on their access rights) were asked to use cryptographic keys.
Such fast deployment was only possible because of using an approach of user access security broker where implementation is done without software development. To learn more about how it can be done and how it will help you address remote work cyber security risks, schedule a call discovery call with us here.