Cybercriminals hunt for medical data. Zero trust in healthcare is the only good security approach to keep the medical system secure. According to a Trustwave report, medical data may cost up to $250 per record on the black market, while stolen payment card data is sold for $5.40. That is why healthcare institutions are becoming the main vector of cybercriminals attacks. How to defend against them? The right approach is to protect the space where usually attacks come the most often so the accounts of all employees of clinics or hospitals.
Zero trust in healthcare
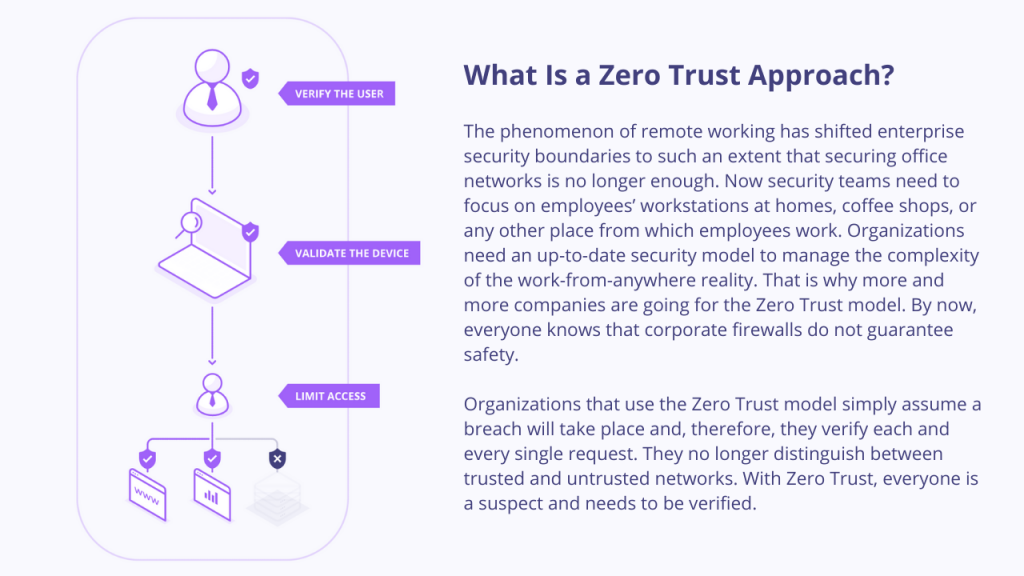
Zero trust security is a cybersecurity concept that implies a total lack of trust in users, systems, or services within the network. What does this mean and how does it relate to the safety of the healthcare industry? Zero trust relies on 100% certainty that the right person is on the other side of the computer, and not a thief who wants to take over your sensitive data.
– Medical data is extremely attractive to cybercriminals. Mainly because intruders know very well how to cash them – says Tomasz Kowalski, CEO, and co-founder of Secfense, which has developed a technology that enables fast and comprehensive implementation of multi-factor authentication (MFA), which is a first step in zero trust implementation in healthcare organizations. – Theft of medical data can threaten the reputation of individuals or institutions and cause enormous damage. That is why all healthcare facilities must remodel their approach to IT security as soon as possible and base it on strict user authorization, restriction of permissions, and limiting access to medical resources in accordance with the principle: never trust, always verify.

One of the latest media attacks against a medical institution was an attempt by intruders to get into the computers of AstraZeneca employees (including those who worked on the Covid-19 vaccine).
North Korean cybercriminals have used phishing and social engineering claiming to be recruiters. According to the Wall Street Journal, the attackers also tried to steal vaccine information from Johnson & Johnson and Novovax, as well as from three South Korean drug makers.
2-Step Verification
Credential theft – employees’ passwords and logins – is one of the most common causes of attacks on medical institutions today.
Cybercriminals usually send an e-mail designed to trick the person into thinking that the message comes from a legitimate source and then obtain credentials. Bad actors also often use WhatsApp or LinkedIn messengers, as happened in the case of the attack on AstraZeneca.
Why is this happening? The healthcare industry is one of the worst when it comes to data security knowledge. Data from Wombat Security’s learning management system shows that 23% of best practice questions are answered wrong on average by medical personnel. Fraudsters know that very well. The difficult period associated with the pandemic only makes it easier for them to get access to extremely valuable information, for which, for example, they can receive a large ransom (ransomware attacks).
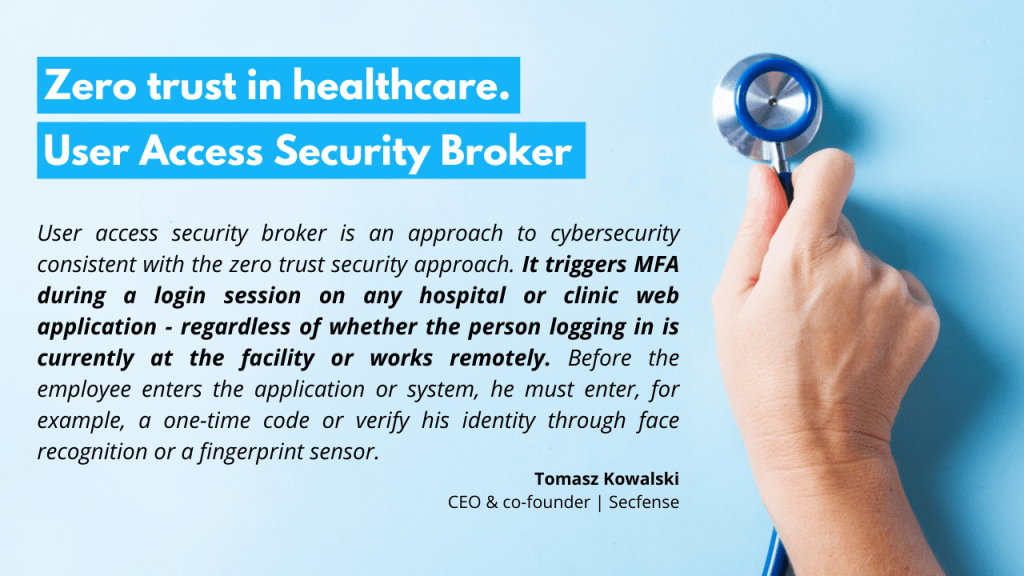
– User access security broker is an approach to cybersecurity consistent with the zero trust security approach. It triggers MFA during a login session on any hospital or clinic web application – regardless of whether the person logging in is currently at the facility or works remotely. Before the employee enters the application or system, he must enter, for example, a one-time code or verify his identity through face biometric authentication (such as face recognition or fingerprint scan)- adds Kowalski.
Multi-Factor Authentication (MFA) Implementation
What’s important is that the integration of MFA takes place without changing the protected application’s code. This basically means that the security broker can add multi-factor authentication on the accounts of all employees in any number of applications without any subsequent support for IT specialists, who are constantly lacking in the medical sector. It also allows for convenient scaling – simple and quick adding of users and protected resources, regardless of their number and complexity. This is important in the case of dynamically developing private hospitals and medical clinics.
– Organizations do not have to share any of their information with third parties – strong authentication can be easily applied to the current infrastructure without long and tedious programming – adds Tomasz Kowalski.
Cybercriminals use the pandemic very efficiently and target the weak points of the healthcare system. Therefore, medical facilities must ultimately do a very difficult task and protect not only selected but in reality, all applications used by their employees on a daily basis. This could mean using advanced analytics to track identities on their network, multi-factor authentication, and enforcing “least privilege policies” for specific accounts, so basically following healthcare zero trust cybersecurity guidelines.
One thing to remember – flexibility, scalability, and speed of response in the case of precise and increasingly sophisticated attacks will be a key factor influencing the final result. Well-thought-out choices in this context really pay off. The costs of healthcare attacks are growing exponentially as prolonged system downtime not only hampers but often paralyzes medical care for patients.
