There are a lot of vendors on the market that are offering passwordless solutions. But what does the so-called passwordless really mean? Will the login process disappear? What will the password be replaced with? How can we protect our data if the password will be out of the picture? Let’s dig deeper into this.
What is a Passwordless sign-in?
There are a lot of marketing pitches that promote a passwordless future. Does that mean that users really don’t have to remember anything, or does this mean that they’re going to be using some other form of authentication? Will futuristic-sounding biometric authentication replace passwords? Or will physical authenticators or combinations of those things create some form of passwordless experience?
So what is passwordless? Well, think of a physical authenticator that we all know – a door key. We use this ancient technology all the time. We don’t use this approach very often, though, when it comes to online access. And there are some good reasons for that.

Is Passwordless authentication safe?
The threats related to using just a physical authenticator are pretty obvious. It could be stolen, it could be lost, it could be broken, and it could also be duplicated. Generally, you would notice if you didn’t have your key for a little while, it feels a little different in your pocket unless you’ve got dozens of them.
Now think that the key could be on your phone. Or even the phone could be your key. Same thing with a laptop. If your electronic device is your key, then if somebody borrows it from you, this key could be extracted and stolen without your knowledge. So as a result, organizations or online vendors tend don’t use physical authenticators as password replacements.
So, in theory, your cellphone could serve you as a passwordless authenticator. But would it serve the purpose? Would it make the login process smooth WHILE maintaining or improving security? Not really.
So unless the device is used as a second factor (in Two-Factor Authentication), it’s not really an improvement in security like so many of the password vendors are promising but rather a not-so-safe alternative.

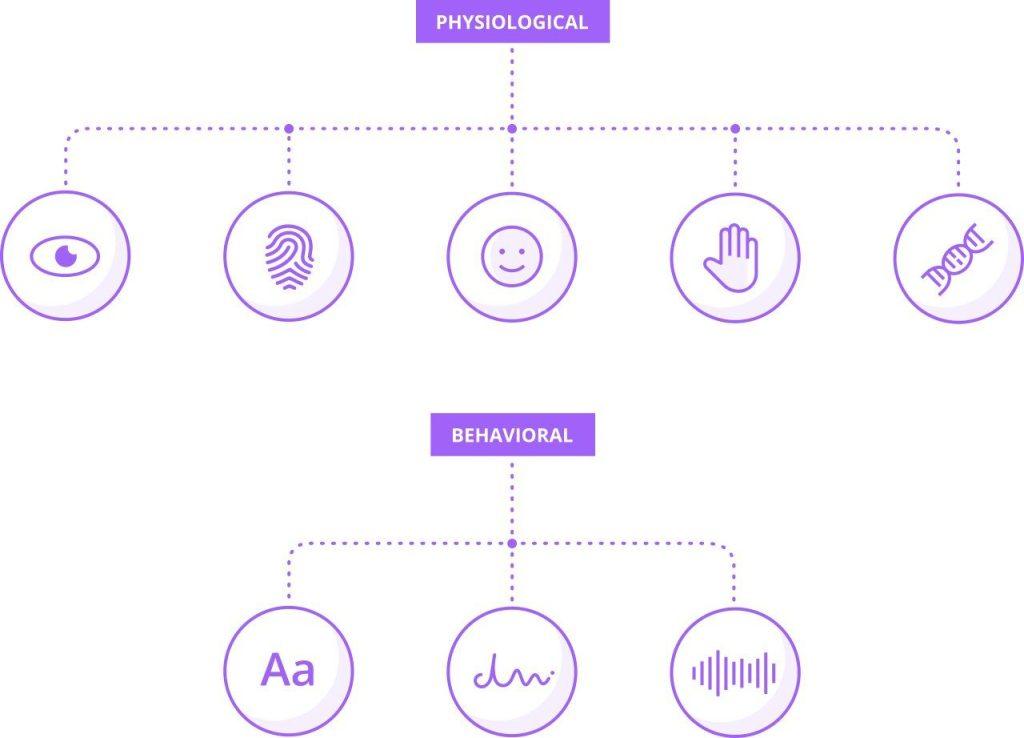
What is physiological biometrics?
Another approach to passwordless authentication could be biometrics. A lot of people think that biometrics is the ultimate security, but the truth is very far from it. The problem with biometrics is that almost all of the biometric modalities that exist have ways to be obtained by a bad actor or even unintentionally.
Fingerprint Biometrics
A fingerprint? We leave it on everything. So if you go to a restaurant, the waiter could take a copy of your biometric fingerprint if they really wanted to and then use it against your will.
Eye biometrics and Iris recognition
A similar thing with iris patterns. In fact, iris patterns are fairly easy to obtain, especially if the person is blue-eyed. With just a high-resolution photo of the person, iris patterns can be copied and then used to authenticate.
Biometrics are also not replicable. So if somebody copies your fingerprint or your iris pattern, this is not something that you’re able to change.
The other issue is that biometrics aren’t a deterministic authentication method or a deterministic factor – it’s more like a measurement. Think of a password. It could either be right or wrong. There’s no halfway. 99% correct combination of letters and digits will not let you get through. If you use your device, a key, or phone, or another physical authenticator, then it will either have the right key or the wrong key on it. But biometrics is different. if it’s close and the system believes that it’s really you, then it will accept you.
Biometric authentication is pretty common now. It’s being used a lot with phones that either have fingerprint or face recognition sensors. The good thing about biometric authentication in smartphones is that the biometric template of what it’s comparing against and the comparison can be all embedded in one device.
Biometric authentication, however, is not something that could be used broadly on all sorts of devices. It will most likely never be possible to go to a shop, buy some food, put your fingerprint on the sensor, and then just leave. Why? Because of the irreplaceability of biometric features. Because if your fingerprint could be remembered and stored on shopping equipment or, in fact, other types of equipment, POS, ATMs, etc., then anyone that could copy your fingerprint could basically become you and authorize all purchases, withdraws, and other operations without any problem.
Combining PIN and Biometric Authentication
But what if your fingers get dirty or you’re wearing a facemask? In such a case, the biometrics would not work. When your face or fingerprint is not recognized, your phone immediately asks you to authenticate with a PIN. Why?
Well, vendors most often give a biometric authentication option together with an option to exchange it with a PIN. If this combination is in place, then if somebody got your phone, he or she would still need to know your PIN to enter it. Let’s say a hacker intends to use a copy of your fingerprint and fails to authenticate on the first or second attempt. Then he or she will be asked to give a PIN which is the second step of protection and yet an additional burden for the attacker.
Of course, there’s a way to hack a PIN code, but it takes time and effort. And the goal of cybersecurity is to make the attacker’s life hard enough so that he or she is not interested in breaking it. So that the struggle is not worth the attempt. So it’s better for the cybercriminal to pick an easier target than work hard to break through yet another fence.
Biometrics keeps improving; there are fewer and fewer false accept rates which is great. However, the fact that biometric features are not replaceable will most likely never allow this authentication method will replace passwords and be the only factor to use to let you access online resources or approve online purchases.
Another reason for vendors to use biometrics together with a PIN code is a really high false accept rate of the biometric. Most of the devices will give a user only one or a few attempts before they will switch from biometric to PIN. Biometric sensors don’t give the same degree of security as a cryptographic key.
Biometrics is really a convenience factor rather than a security factor. Authenticating with PIN and biometrics both have weaknesses that are different from one another, but they both are not free from flaws, that’s for sure.

Passwordless again
Pins are really simpler or weaker passwords. But as long we’re using them as a second factor, for example, combined with a physical authenticator, then it’s still way better than even the most complicated password. Even the worst 2FA is better than the best password.
There are big databases of hashed passwords that get stolen every day. There are tons of really great passwords there. But it doesn’t really matter how complicated your password was if it got stolen and simply copied and pasted to compromise your account.
The PIN can be that simple because apart from PIN, you actually need a local, physical device. So the bad actor would need to have both your PIN and your device to get through, which makes it twice as hard to obtain two factors than simply one.
But let’s say the bad actor has your device, and he or she wants to attempt to brute force your phone. That’s why the vendors offer a certain limit on how many tries a user can make during a given hour or a day.
There are other combinations of authenticators that are passwordless as well. A physical authenticator that will send you a text message. It could be a physical authenticator and an email. Both are very widely used, but both offer limited security as both your phone number and email address can get easily compromised.
So. a Passwordless future depends on what you call a password, really.
Is PIN a password as well?
Or when they say passwordless, what do they really mean password… AND something else. Which in this case, makes all the second-factor vendors passwordless solutions.
The big benefit of 2FA for an everyday user is that if you’re using two-factor authentication, you don’t really need to think that much about making your password strong, as the second factor does the job for you. So it’s enough that you have some password, any password, and as long as the second factor is strong enough, it will be really hard (discouraging) for an attacker to point you out as a potential victim.
How do you implement Passwordless authentication?
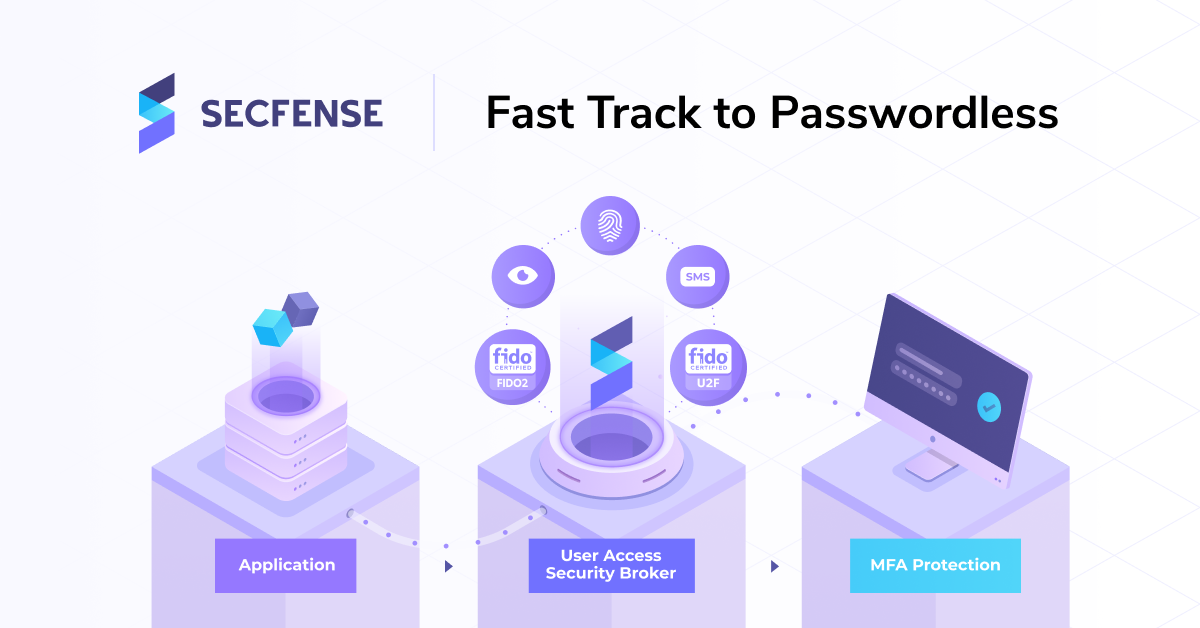
There are a lot of cybersecurity vendors who offer FIDO2 standards or some other form of strong authentication. Most of them do not need access to client credentials, so they can stay safe in client infrastructure (no need to share any data with a third-party vendor). However, in most cases, the implementation of passwordless authentication across the entire company is hard or, many times, simply impossible.
There’s also a problem related to keeping one method of authentication and the inability to switch to a different one. If a company decides to go with one authentication method, it’s hard to shift to a different one when such a necessity will come up. One of the best ways to tackle this is to go with the user access security broker approach. Security broker allows organizations to deploy and scale any authentication method on any number of applications. You can start using passwordless on top of any app or any IAM that your company uses. The deployment is frictionless, and any authentication method can be changed with any other at any time. You can order free tests of passwordless transformation with Secfense here. The test usually takes 7 days, and after the POV (proof of value), you will know exactly how your infrastructure will work with passwordless authentication. You can also book a 15-minute demo, and you will see how we add FIDO MFA to one of your apps in minutes which is a first step to going full passwordless.