Passwordless authentication is a new buzzword that will be repeated over and over in the cyber-marketing space in 2022. While the previous years were marked by the zero-trust security concept and multi-factor authentication (MFA), 2022 will definitely be the year of getting rid of passwords wherever it’s possible.
Who needs passwordless and login without a password?
Okay, but while for the average smartphone or laptop user the ability to log into their device without a password is an obvious convenience, does this ‘revolution’ really come down to the comfort of use?
What is passwordless authentication?
A passwordless authentication is an approach to authentication in which the traditional password is replaced by alternative authentication methods.
Methods are used in the plural, not by coincidence. In virtually all cases where companies decide to abandon passwords, they also decide to replace them with not one, but several authentication methods often based on biometric authentication.
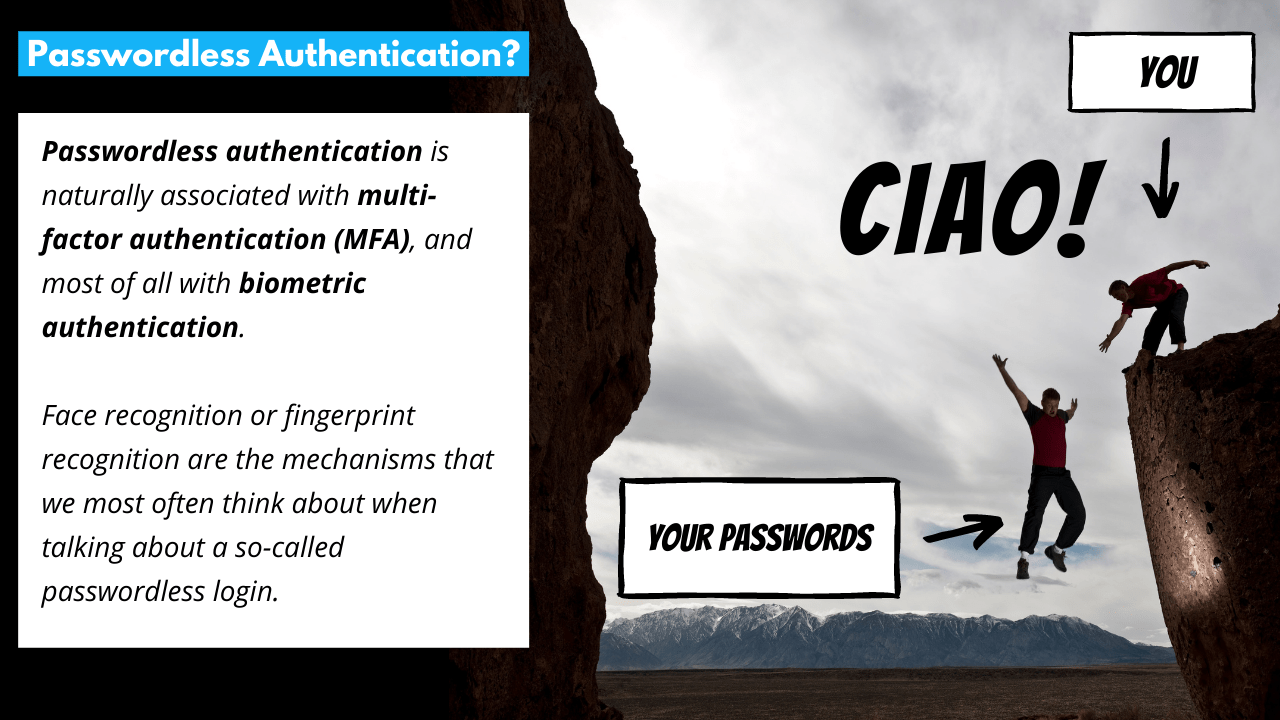
Is passwordless and multi-factor authentication the same?
Passwordless authentication is naturally associated with multi-factor authentication (MFA), and most often with biometric authentication. Face recognition or fingerprint scan are the mechanisms that we most often think about when talking about logging in without a password.
Companies that move away from passwords most often reach out for FIDO2, the open web authentication standard, (some of you may have heard also about its predecessors – U2F cryptographic keys). Devices that support the FIDO2 standard allow the user to authenticate using face or fingerprint recognition mechanisms.

Why do companies switch to passwordless authentication?
We already know what passwordless authentication is and we know that it makes logging in much more convenient compared to passwords. Is convenience the main reason why this big shift in the authentication approach is taking place?
Is passwordless authentication safe?
At this point, we come to the key issue and one of the most important reasons why passwords become a thing of the past and are replaced by passwords login. That reason, of course, is security.
Security is the key argument mentioned by the respondents in the survey conducted by the Cybersecurity Insiders. In the survey, as many as 91% of respondents mentioned the elimination of the problem of using stolen or broken passwords as the most important reason for moving away from passwords.
Convenience, of course, is also very important. It’s the second most voted thing with 64% of the votes. Still, it is the desire to avoid password-related cyberattacks that drives the transition to passwordless in the majority of organizations. Cybersecurity teams want to completely eliminate passwords and finally, they have the right toolkit to do that.

Why is passwordless authentication so secure?
Okay, we already know that passwordless authentication eliminates all password-related pains and attacks. But what do multi-factor authentication and passwordless authentication offer, making them a better alternative to passwords?
Multi-layer security
The first thing we mentioned at the beginning of this article is that passwords are rarely replaced with just one component. Logging in to the application using a smartphone already gives us several layers that we are not even aware of. First of all, the face or thumb recognition, so biometric authentication only works on a specific device (unlike passwords that can be used from any device). Secondly, phones often remember the location, so if you log in from a different network or latitude, the application may send you a push with a re-authentication request or send a one-time code. In case the camera does not recognize the face, the user will be asked to enter the PIN code. So in this specific case, there are already 5 different authentication factors in place:
- Inherence factor (the user must be physically in front of the camera to scan their face).
- Knowledge factor (user must know PIN).
- Location factor (user must be in a known geolocation device or network).
- Time factor (the user has a specified time to enter the code received via SMS).
- Possession factor (the user must have a smartphone for which he will receive an SMS code).
Cryptography and the open FIDO2 web authentication standard
We write quite extensively about FIDO2 on the pages dedicated to this extraordinary authentication standard. In a nutshell, FIDO2 completely eliminates the risk associated with phishing attacks and the use of weak or stolen passwords. FIDO2 authentication prevents the user from logging in to a fake domain. Even if a person would fall victim to a masterfully conducted social engineering attack, with the user’s account secured with FIDO2, it is not possible for the criminal to get through. The criminal cannot log into the user’s application without the physical presence of the user, who physically places his thumb or scans his face at the time of login.
How to implement passwordless authentication?
If passwordless authentication is a much better and safer form of authentication, why have only a handful of companies successfully implemented this approach? The answer as always comes down to resources. Time, work, and costs.
Two-factor authentication (2FA) implementation on some core systems is still a challenge for many companies. Not to mention rolling out 2FA as a default on all applications within the company.
There are many ways to start the journey to passwordless and erradicate passwords altogether. Secfense came up with the approach called uses access security broker, i.e. a technology that enables the non-invasive implementation of any method of multi-factor authentication (MFA) on any application without touching the protected application’s code.
Implementation of passwordless and login without a password with the user access security broker
We have written a lot about the concept of user access security broker on the page dedicated to this approach, to which we refer. In a few sentences, the main advantages of the broker are:
- flexibility in selecting strong authentication methods – the ability to easily implement any multi-factor authentication method available on the market
- independence of the strong authentication method from the application – MFA authentication is added to the application without any interference with the code of the protected application
- scalability of the implementation – the entire organization can be covered by multi-factor authentication, and not only selected applications, as in most organizations
- Eliminate production costs – quick implementation that does not require any software development work at any stage
More about passwordless authentication
On our pages, we have devoted a lot of space to passwordless authentication and the easy implementation of multi-factor authentication in organizations. If you find this article interesting, we encourage you to read our other articles related to the subject, in particular:
- Your password has expired… it’s time for it to go extinct
- Secfense and the path to passwordless
- Why bad use of a VPN can be dangerous?
- What is a U2F key and how to use it to protect your data?
- Secfense – passwordless authentication improves the level of cybersecurity in enterprises
At any time, you can also ask us a question, propose the topic of the next article, or simply share your opinion on what we are doing here.
